


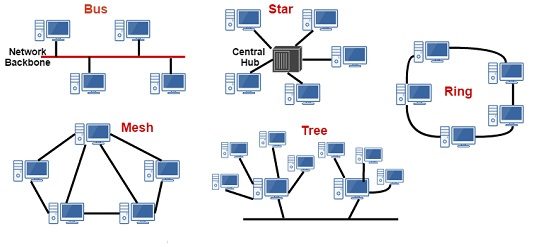
III. RING topology: A ring topology is a topology in which each node connects to exactly two other nodes, forming a single continuous pathway for signals through each node. A token ring network is a network in which all computers are connected in a ring topology and a bit-passing or token-passing scheme is used in order to prevent the collision of data between two computers that want to send messages at the same time. Token Ring network is ideally used in LAN (Local Area Network).
--> Data is quickly transferred without a ‘bottle neck’. (very fast, all data traffic is in the same direction) [Justify: One node is directly connected to only two neighboring nodes and hence it can pass the data directly without bottleneck (choking/blockage of network)]
--> Adding additional nodes has very little impact on bandwidth. [Justify: Adding one node simply means connecting an external node to two neighboring node and thus it will have minimum impact on bandwidth as it is not passing data, to any other node in the network, directly]
--> If any of the nodes fail then the ring is broken and data cannot be transmitted successfully. [Justify: Just like a necklace of pearl, if one pearl breaks out, the whole necklace breaks. same logic can be applied in this topology.]
--> It is difficult to troubleshoot the ring. [Justify: All the nodes are only connected to 2 nodes only and there is no single point of reporting like in star topology and hence it becomes difficult to identify which node is defective and thus hard to troubleshoot, similar to bus topology.]
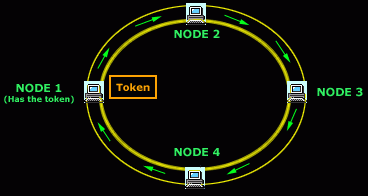
IV. TREE topology: A tree topology combines characteristics of linear bus and star topologies. It consists of groups of star-configured workstations connected to a linear bus backbone cable. Thus, a tree network is a bus network of star networks.
 Advantages:
Advantages:
--> Expansion of Network is possible and easy. [Justify: Adding of system in bus topology is easier as the connection is only to be made to the backbone cable, similarly in tree topology, a complete star topology would be treated as a node and is added on the backbone and thus expansion is not complicated.]
--> Each segment is provided with dedicated P2P wiring to the central hub. Thus no Central point of failure. [Justify: Unlike Bus topology which had T-CONNECTOR for connection of every node, a hub or an advanced sort of connector is used in tree topology. This connector gives a Point to Point (P2P) connection for all the star topologies (referred to as 'segments') with the backbone cable.]
--> As more and more nodes and segments are added, the maintenance becomes difficult. [Justify: Similar to bus topology, for heavy traffic, single backbone line does not provide efficiency in network]
--> Scalability of the network depends on the type of cable used. [Justify: The backbone cable type plays a major role as the medium must not get damaged due to heavy load of data.]
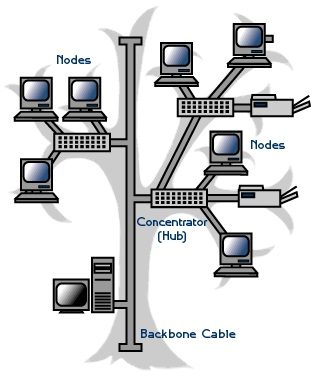
V. MESH topology: A mesh network is a network topology in which each node relays data for the network. All mesh nodes cooperate in the distribution of data in the network. In a full mesh topology, each network node (workstation or other device) is connected directly to each of the others. In a partial mesh topology, some nodes are connected to all the others, but others are only connected to those nodes with which they exchange the most data.
--> Data can be transmitted from different devices simultaneously. This topology can withstand high traffic. [Justify: All the nodes are connected to either every other node or to the node with most exchange of data and thus high traffic of data will not create congestion in the network as there are multiple paths for connection.]
--> Expansion and modification in topology can be done without disrupting other nodes. [Justify: Similar to ring topology where addition of one node would mean that it must be connected to two nodes while in Mesh, one node must be added to all the other nodes or some of the nodes depending upon partial or full mesh configuration. Thus adding a node is not problematic but creating this whole setup is tedious.]
--> There are high chances of redundancy in many of the network connections. [Justify: All the nodes are directly connected and hence there may be repetition of data.]
--> Set-up and maintenance of this topology is very difficult. Even administration of the network is tough. [Justify: Every node is connected to every other node and this setup is very difficult to form and maintain and it also makes it difficult to identify that which node is exactly creating faults and specifically which part of data is at fault.]
***Thus answering all the basic rhetorical questions such as "What", "Why" (A-B-C of Networking: Part-1) and "How" (A-B-C of Networking: Part-2, A-B-C of Networking: Part-3A and A-B-C of Networking: Part-3B) of networking in 4 blogs.***