


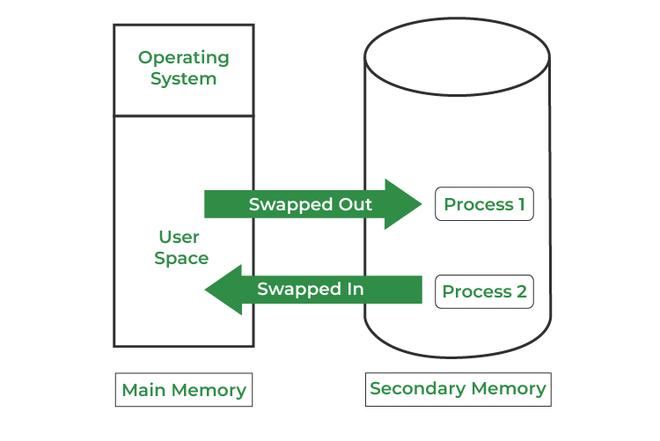
Memory management in OS is a technique of controlling and managing the functionality of Random access memory (primary memory). It is used for achieving better concurrency, system performance, and memory utilization.
Memory management in operating systems involves allocating and deallocating memory resources efficiently to optimize system performance. It includes tasks such as memory allocation, tracking which parts of memory are currently in use, and freeing up memory when it is no longer needed.
Effective memory management is crucial for ensuring stability, responsiveness, and overall efficiency of computer systems.
In the realm of memory management, distinguishing between logical address space and physical address space is paramount:-
Logical Address Space encompasses the range of addresses that a CPU can generate. This is the perspective from which a program "sees" its memory. For instance, if a computer has 4 GB of RAM, the logical address space might span from 0 to 4 billion. However, it's important to note that this space is not entirely occupied by physical memory. Instead, it serves as a convenient and abstract representation.
Physical Address Space, on the other hand, is the actual physical location in the memory hardware where data is stored. It constitutes the tangible address of a storage cell in RAM. In our previous example, if the RAM modules consist of 4 billion cells, the physical address space would correspond to each of these individual cells.
Example: Consider a scenario where a program attempts to access memory address 'a' in its logical address space. The MMU translates this to the corresponding physical address 'b' and retrieves the data from the actual RAM location. This abstraction allows for efficient multitasking and memory allocation.