


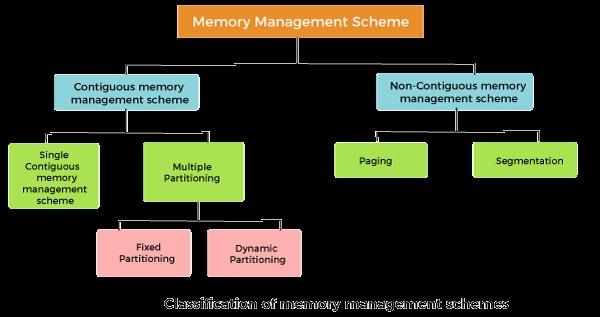
Memory management in an operating system (OS) is like a librarian managing books in a library. Here’s how it works in simple terms:
1. **Allocation and Deallocation**: Imagine programs as people borrowing books (memory) from the library. The librarian (OS) gives books to people when they need them and takes the books back when they’re done.
2. **Memory Protection**: Each person should only read their own books and not mess with someone else’s. The librarian ensures that people don't take or modify each other’s books.
3. **Memory Sharing**: Sometimes, several people might need to read the same book. The librarian lets them share it instead of giving out multiple copies, saving space.
4. **Virtual Memory Management**: If the library runs out of physical space (RAM), the librarian can use some space in the back storage (hard disk) to keep extra books. This makes the library seem bigger than it really is.
5. **Memory Mapping**: The librarian can make some books available quickly by placing them in a special, easy-to-access area. This is useful for frequently used books.
6. **Garbage Collection**: Sometimes, people leave books lying around when they’re done. The librarian goes around and picks up these unused books to put them back on the shelves, making room for others.
Overall, memory management ensures that programs run smoothly by efficiently handling the computer's memory, much like a well-organized library where everyone can find and use the books they need.