


Memory management is the process of controlling and coordinating a computer's main memory. It ensures that blocks of memory space are properly managed and allocated so the operating system (OS), applications and other running processes have the memory they need to carry out their operations.
As part of this activity, memory management takes into account the capacity limitations of the memory device itself, deallocating memory space when it is no longer needed or extending that space through virtual memory. Memory management strives to optimize memory usage so the CPU can efficiently access the instructions and data it needs to execute the various processes.
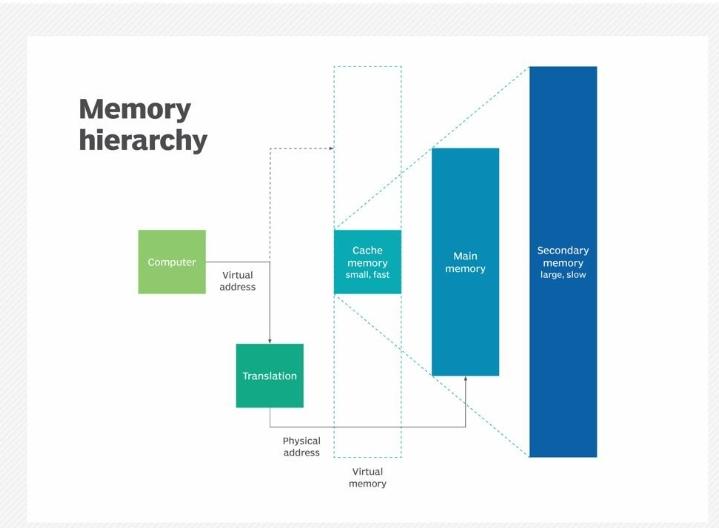
Memory management operates at three levels: hardware, operating system and program/application. The management capabilities at each level work together to optimize memory availability and efficiency.