ASSIGNMENT- 2 Srushti Sanghani
53003220007
Traditional Unix System
Introduction to Unix
Unix - trademarked as UNIX is a multiuser, multitasking operating system (OS) designed for flexibility and adaptability. Originally developed in the 1970s, Unix was one of the first OSes to be written in the C programming language.
History of Unix
- It was developed in the 1970s by Ken Thompson, Dennis Ritchie, and others in the AT&T Laboratories. It was originally meant for programmers developing software rather than non-programmers.
- Unix and the C were found by AT&T and distributed to government and academic institutions, which led to both being ported to a wider variety of machine families than any other operating system. The main focus that was brought by the developers in this operating system was the Kernel. Unix was considered to be the heart of the operating System.
Unix Architecture
The Unix architecture has 4 layers.
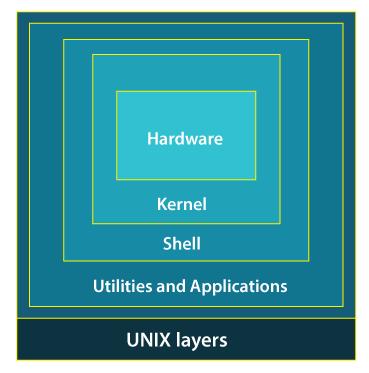
- Hardware - Hardware is the most simple and least powerful layer in the Unix Architecture. Hardware is the components that are humanly visible.
- Kernel - This is the most powerful layer of the Unix architecture. The kernel is responsible for acting as an interface between the user and the hardware for the effective utilization of the hardware. The main 2 features of the kernel are process management and file management.
- Process Management: The processes that execute within the operating system require a lot of management in terms of memory being allocated to them, the resource allocation to the process, process synchronization, etc. All this is done by the Kernel in Unix OS.
- File Management: File management involves managing the data stored in the files. This also includes the transmission of data stored in these files to the processes as and when they request it.
- Shell - Since the kernel is such an important program of the Unix Operating System, its direct access to the users can be dangerous. Hence, the Shell comes into the picture. Shell is an interpreter program that interprets the commands entered by the user and then sends the requests to the kernel to execute those commands.There are 3 types of shells in the Unix Operating system.
- Bourne Shell (sh) - It is the most widely available shell on Unix OS devices across the world. This was the first shell available in the Unix OS. It is simply called a shell.
- C Shell (csh) - The University of California (Berkeley) developed C Shell is another Unix shell that removes some of the obsolete features or problems from the Bourne Shell. So, it enhances the performance of the Bourne Shell.
- Korn Shell (ksh) - The name of the Korn Shell is based on its creator, David Korn. This shell enhances the C shell further by removing the shortcomings of the C shell and also enhancing the user interaction of the Bourne Shell.
- Application layer - It is the outermost layer that executes the given external applications. UNIX distributions typically come with several useful applications programs as standard. For Example:- emacs editor, StarOffice, xv image viewer, g++ compiler etc.



