Network forensics is a subcategory of digital forensics that essentially deals with the examination of the network and its traffic going across a network that is suspected to be involved in malicious activities, and its investigation for example a network that is spreading malware for stealing credentials or for the purpose analyzing the cyber-attacks. As the internet grew cybercrimes also grew along with it and so did the significance of network forensics, with the development and acceptance of network-based services such as the World Wide Web, e-mails, and others.
With the help of network forensics, the entire data can be retrieved including messages, file transfers, e-mails, and, web browsing history, and reconstructed to expose the original transaction. It is also possible that the payload in the uppermost layer packet might wind up on the disc, but the envelopes used for delivering it are only captured in network traffic. Hence, the network protocol data that enclose each dialog is often very valuable.
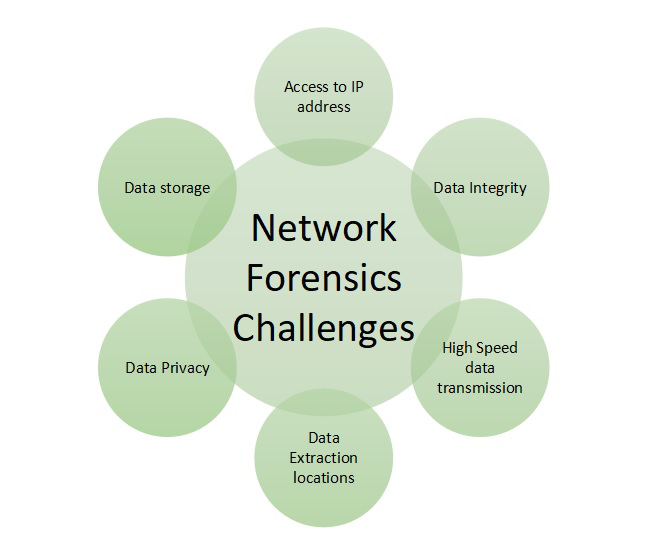
For identifying the attacks investigators must understand the network protocols and applications such as web protocols, Email protocols, Network protocols, file transfer protocols, etc.
Investigators use network forensics to examine network traffic data gathered from the networks that are involved or suspected of being involved in cyber-crime or any type of cyber-attack. After that, the experts will look for data that points in the direction of any file manipulation, human communication, etc. With the help of network forensics, generally, investigators and cybercrime experts can track down all the communications and establish timelines based on network events logs logged by the NCS.
Some processes involved in network forensics are given below: