



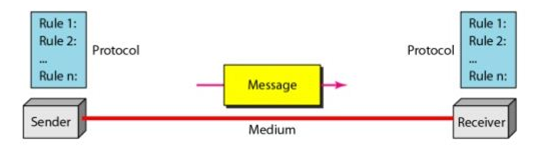
"A-B-C of Networking: Part-1" dealt with the 'A' of "Networking" i.e the concept of networking. Next we move on to "B" which is the *COMPONENT of networking. Components of networking are SENDER, MESSAGE, MEDIUM, PROTOCOL, RECEIVER.
Source: Data Communication, Kwangwoon University
I. SENDER (often referred to as 'transmitter') is the party that sends the message.
II. RECEIVER is the party that receives the message.
III. MESSAGE is any data that is been transmitted from sender to receiver.
IV. {MEDIUM, PROTOCOL} often not considered as single entity but it can be because each of them has a relation. The medium (2 types: wired & wireless (will be discussed later in depth)) is the channel that is used and protocol is the set of rules that are defined for that medium. For example, BLUETOOTH falls under the category of wireless MEDIUM but it implements the PROTOCOL of IEEE 802.15. Thus answering HOW the network is functioning.
These 5 components when placed together to form a network, it becomes important to checkout their arrangements and positioning in the network. In technical terms, the schematic representation of the network must also be taken into consideration and this schematic representation, in networking terms is called as TOPOLOGY of the network (topology description in "A-B-C of Networking: Part-3").
*Component: it implies to the entities or the participants involved in the exchange of data