The information provided by website should be used for educational purpose only, website will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.
 Click on Sniffer
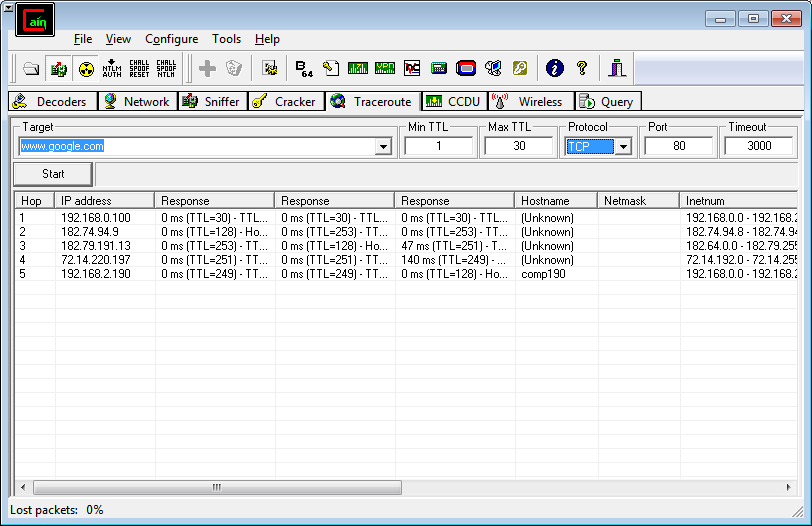
Click on Sniffer 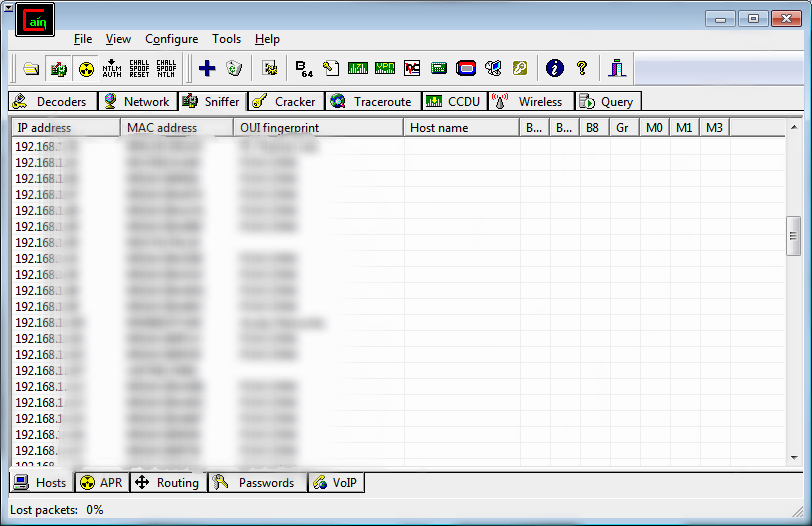 Go to Traceroute tab and enter target ip or domain name to trace the route.
Go to Traceroute tab and enter target ip or domain name to trace the route.
 Click on
Click on 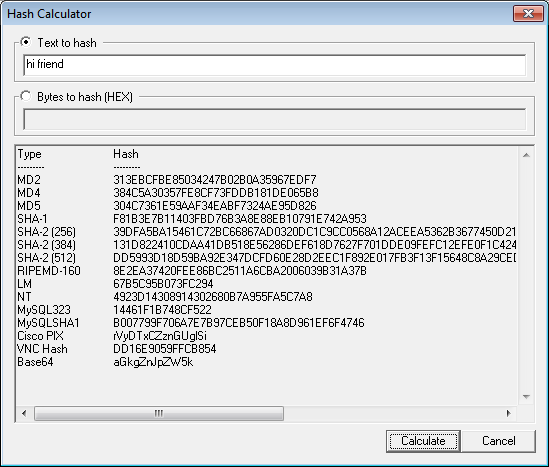
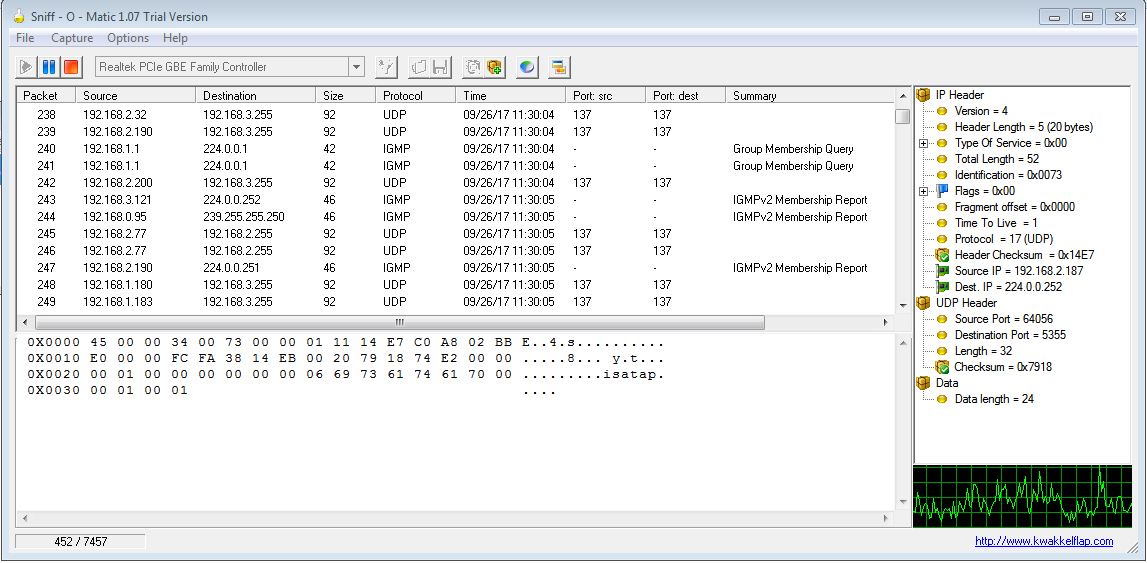
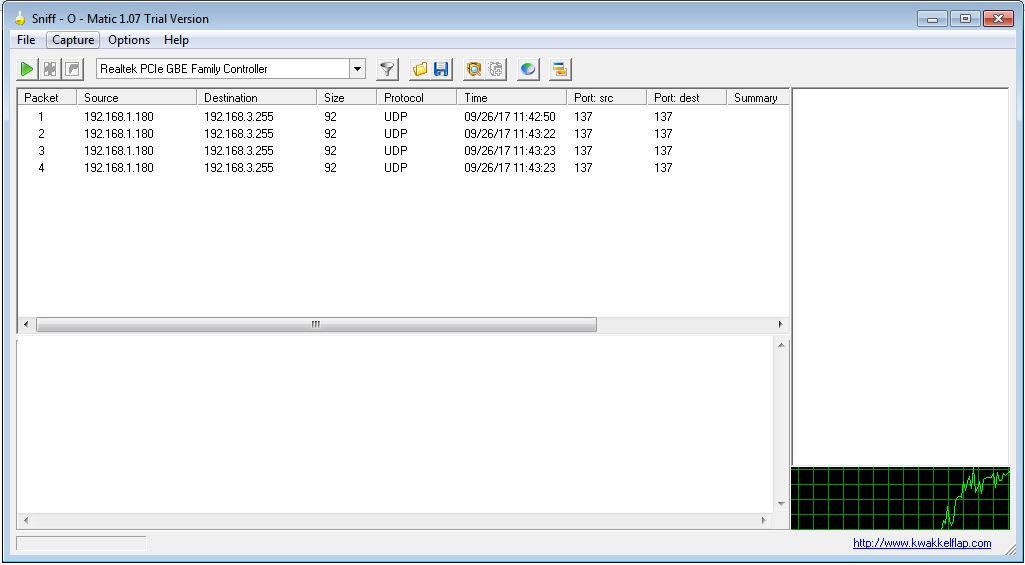
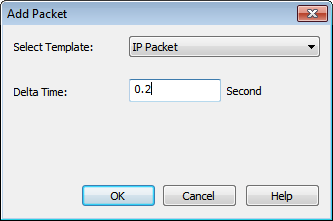 Left panel shows the packets information and right panel shows the total no packet.
Left panel shows the packets information and right panel shows the total no packet.
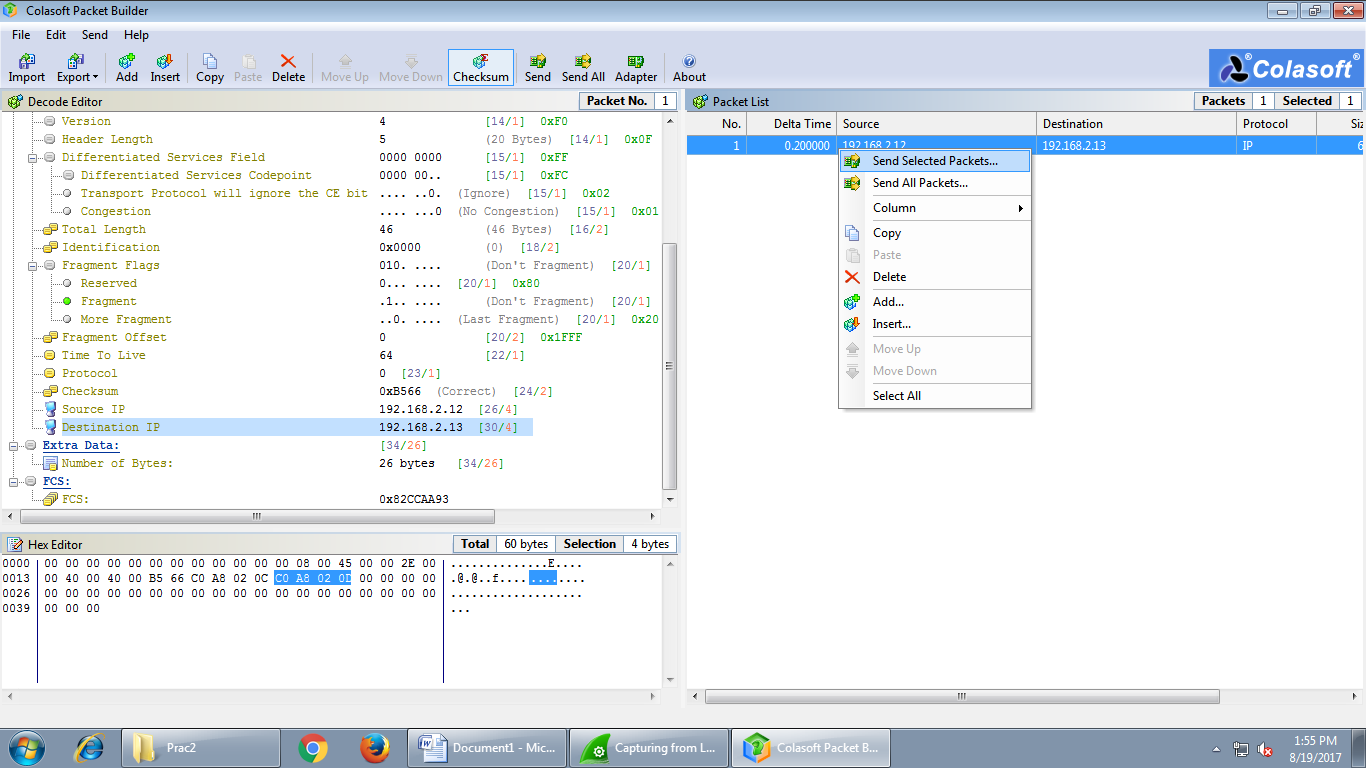
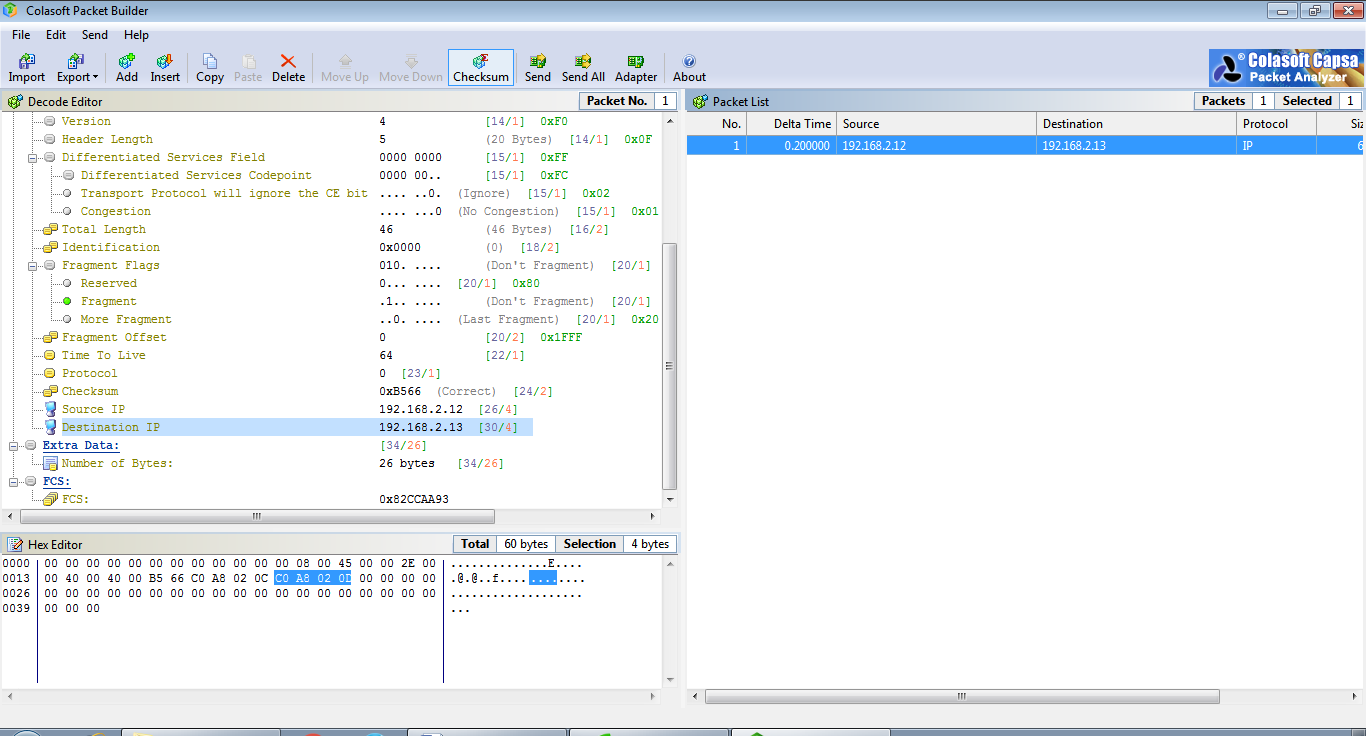 Right Click on the packet and select Send Selected Packets.
Right Click on the packet and select Send Selected Packets.
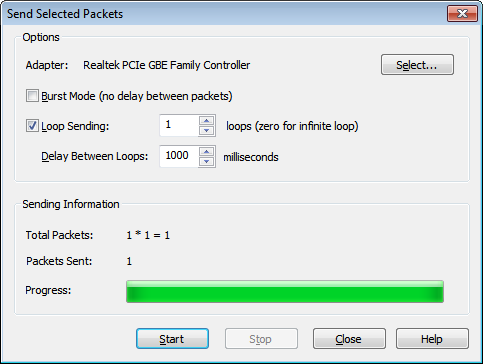
 Check the Loop Sending and click on ‘Select’ to choose Adapter and then Click on start to send packets.
Check the Loop Sending and click on ‘Select’ to choose Adapter and then Click on start to send packets.
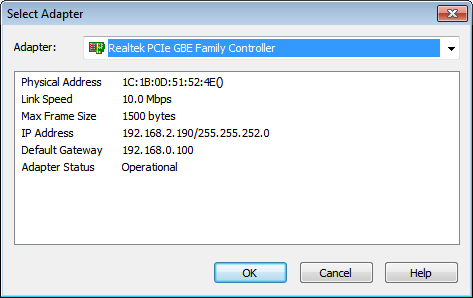
 select interface.
select interface.
 In Wireshark we can see the packets moving from source to it’s destination.
In Wireshark we can see the packets moving from source to it’s destination.
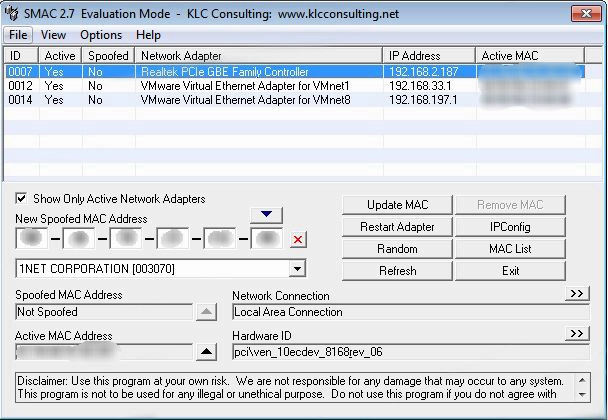
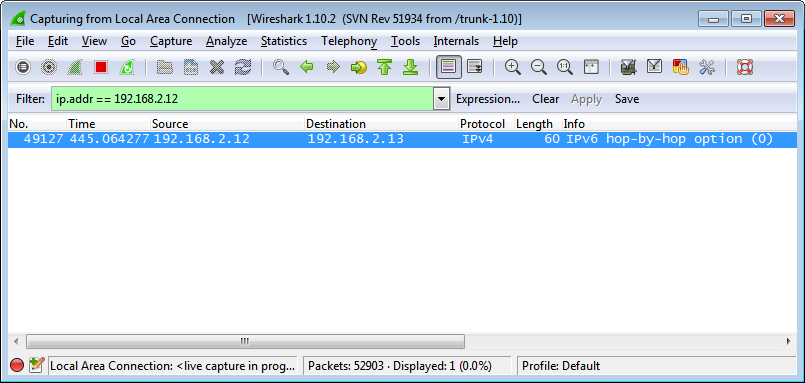 SMAC
Open SMAC tool and select MAC List.
SMAC
Open SMAC tool and select MAC List.
 Select Load List from Sample_MAC_Address_List.txt file and click ok.
Select Load List from Sample_MAC_Address_List.txt file and click ok.
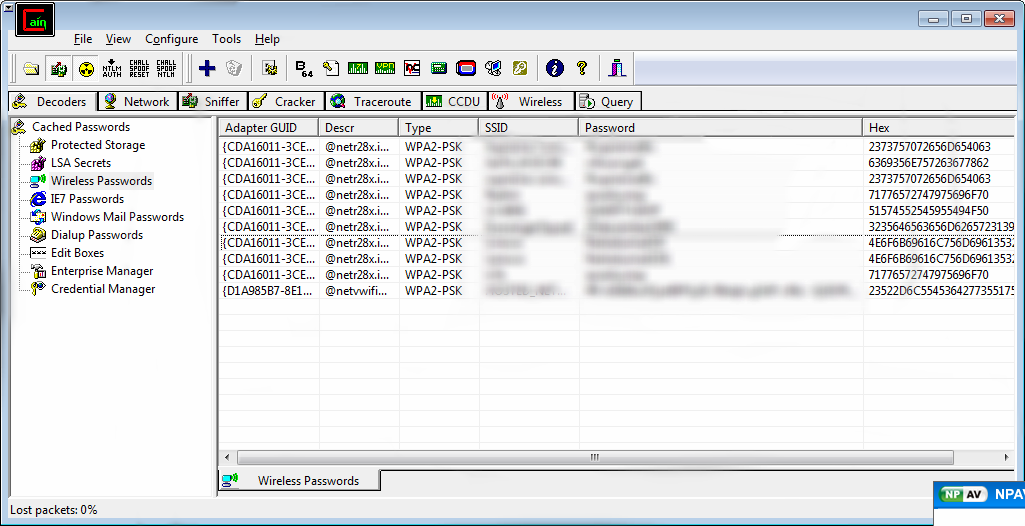
 And the list of MAC address will be displayed and select one mac address.
And the list of MAC address will be displayed and select one mac address.
 Or Click on Random to generate the fake MAC address randomly.
Or Click on Random to generate the fake MAC address randomly.
 Click on to update the MAC Address.
Click on to update the MAC Address.
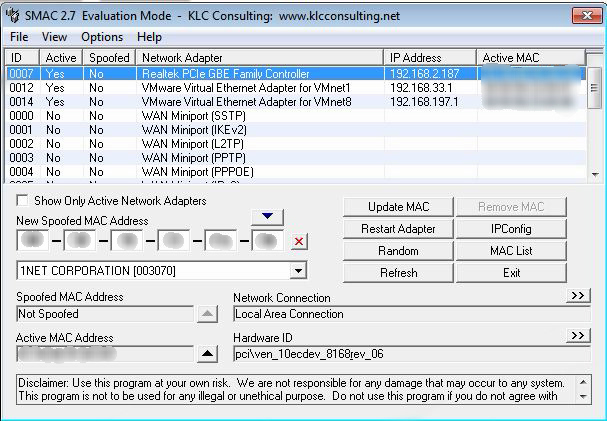
 Unchecke Checkbox to see Inactive Network Adapter.
Unchecke Checkbox to see Inactive Network Adapter.
 We can save the scanned record
We can save the scanned record
 Click on
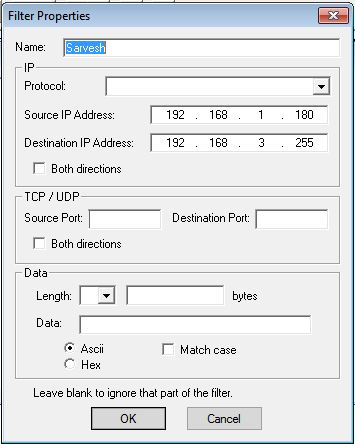
Click on 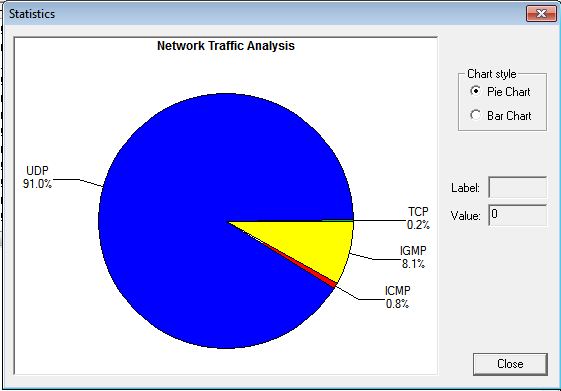 Click on Add to add the filter
Click on Add to add the filter
 Click on OK and re-scan the network.
Click on OK and re-scan the network.
 Click on File --> New Capture
Click on File --> New Capture
 Select Local Area Network Adapter and click OK.
Select Local Area Network Adapter and click OK.
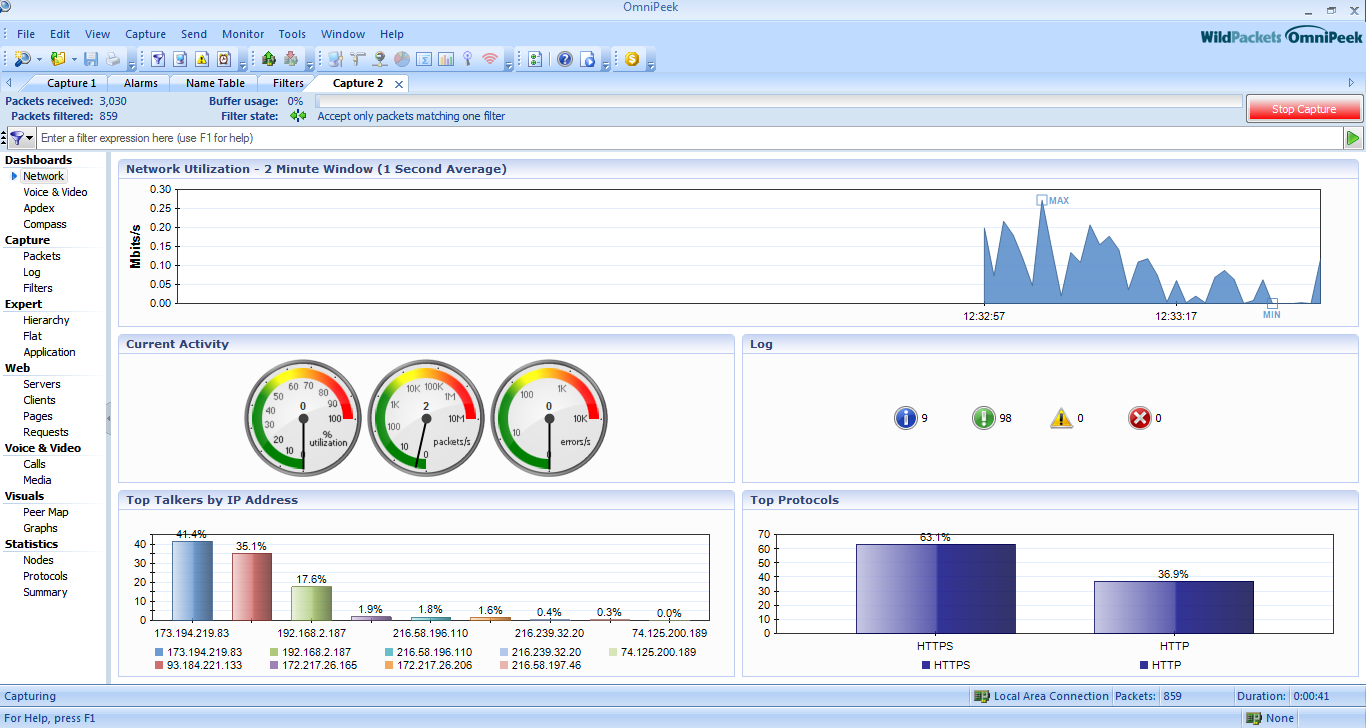
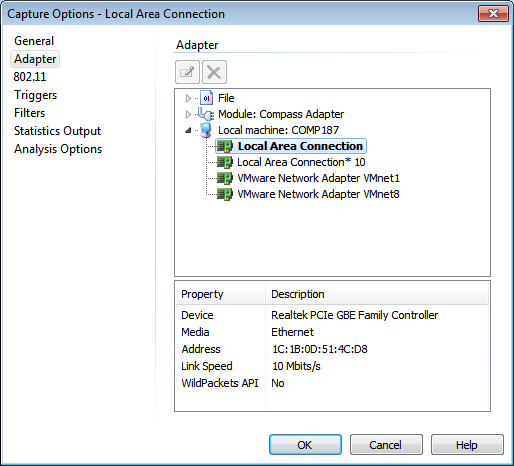 And capture tab will create automatically, and the packet will be captured and we can see them in better GUI Form.
And capture tab will create automatically, and the packet will be captured and we can see them in better GUI Form.
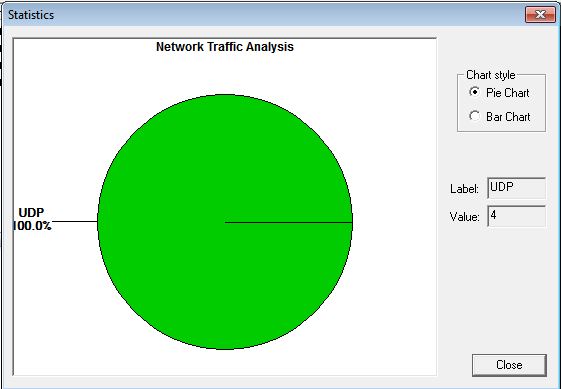
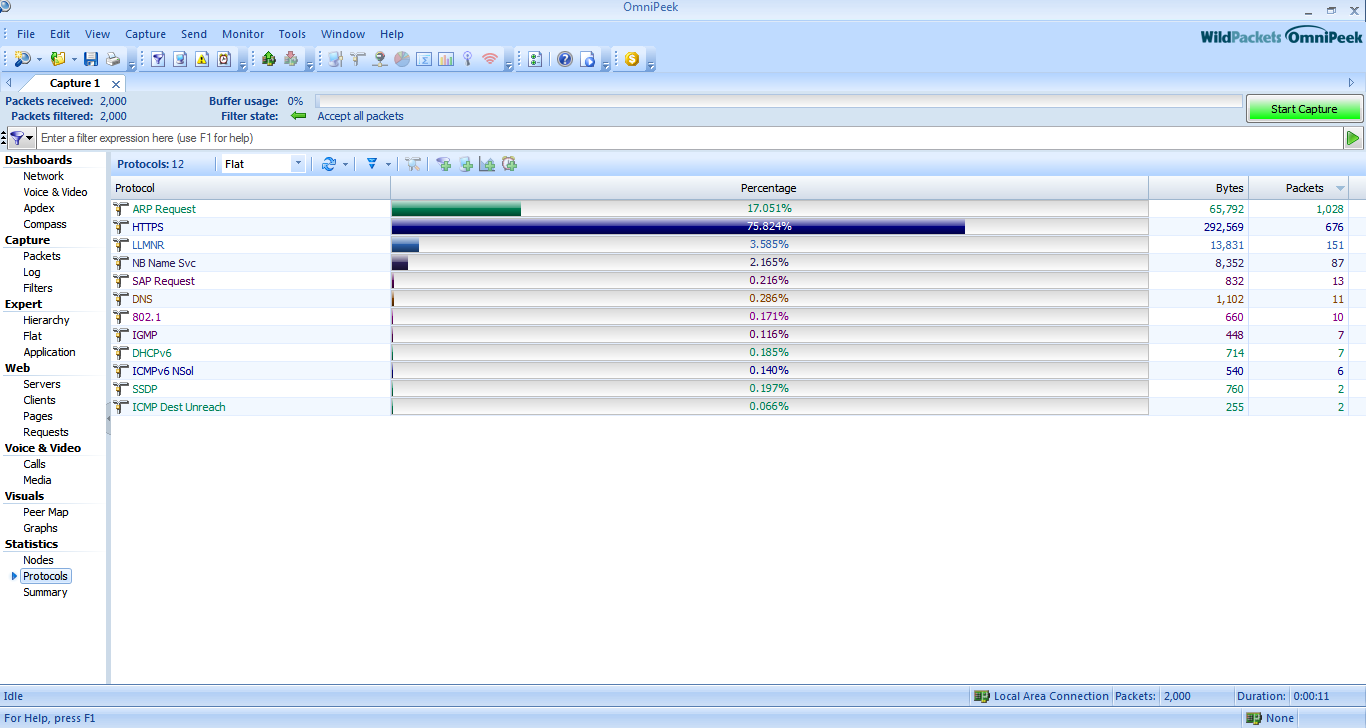
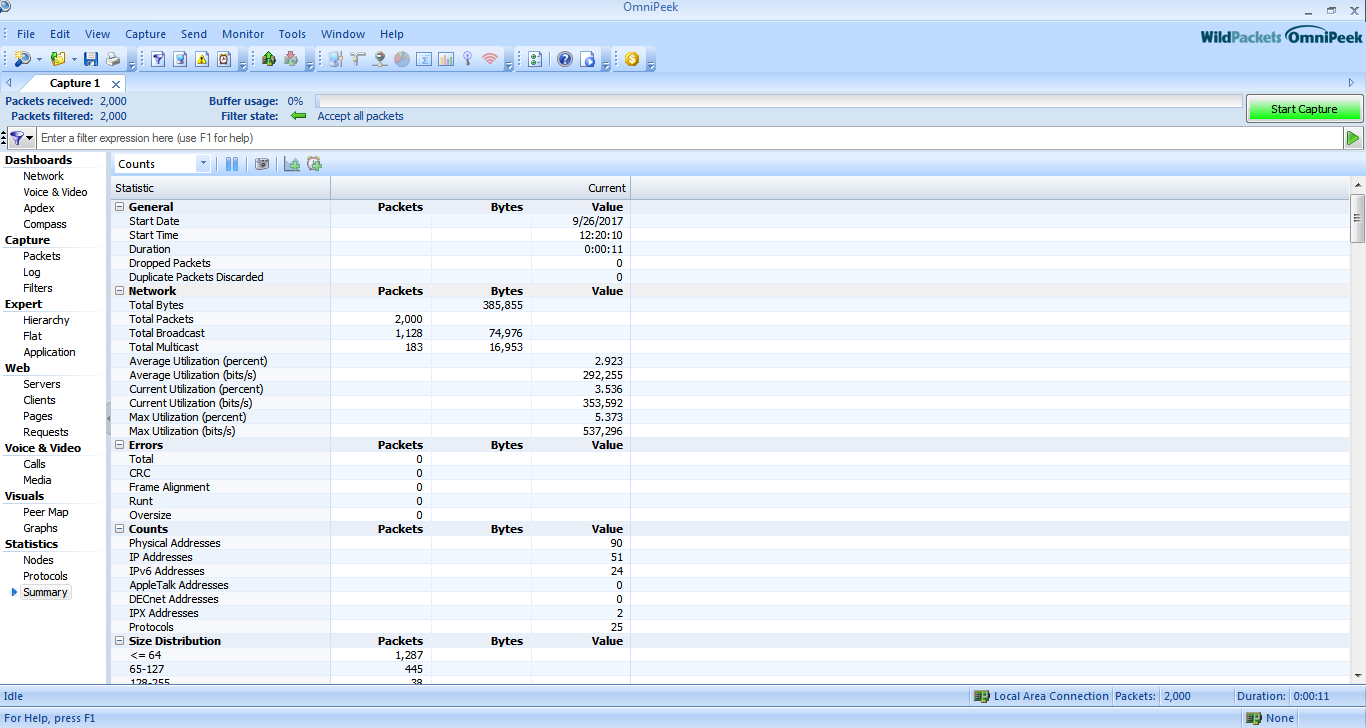
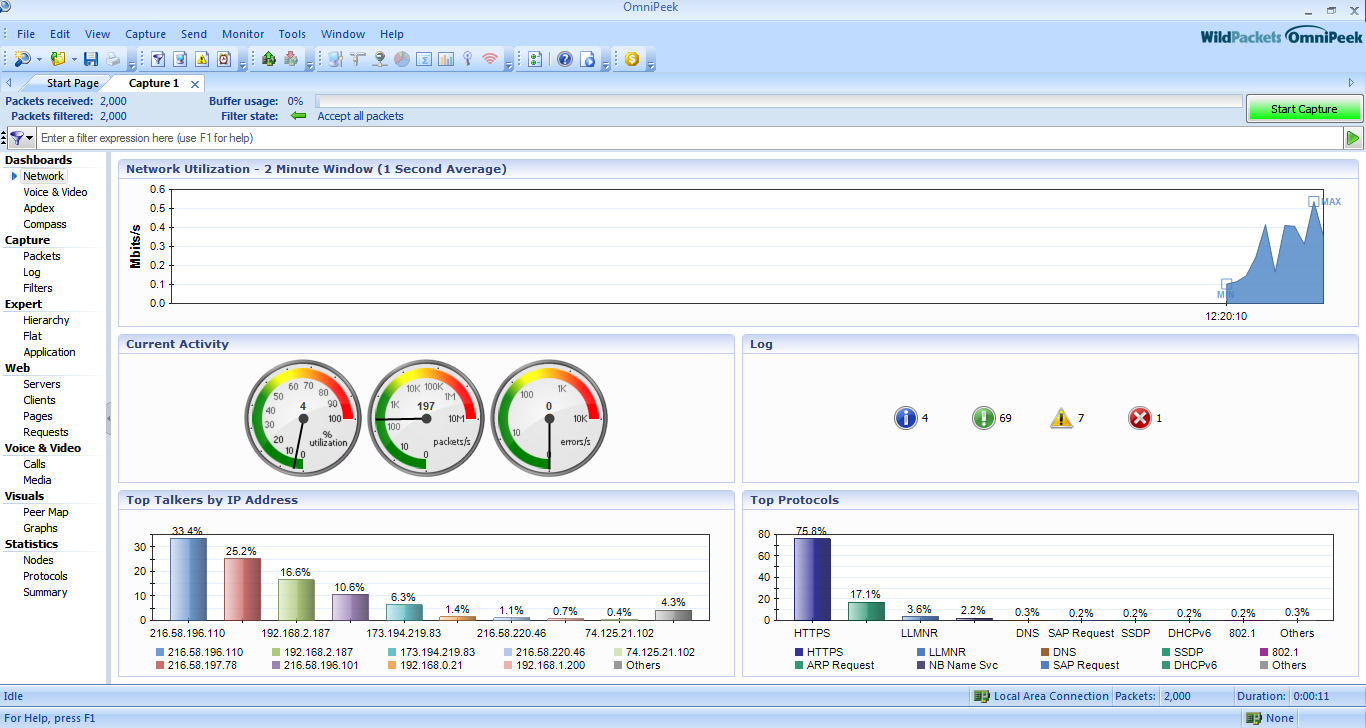 We can analyse different parameters given in the Dashboard of the tool.
We can analyse different parameters given in the Dashboard of the tool.
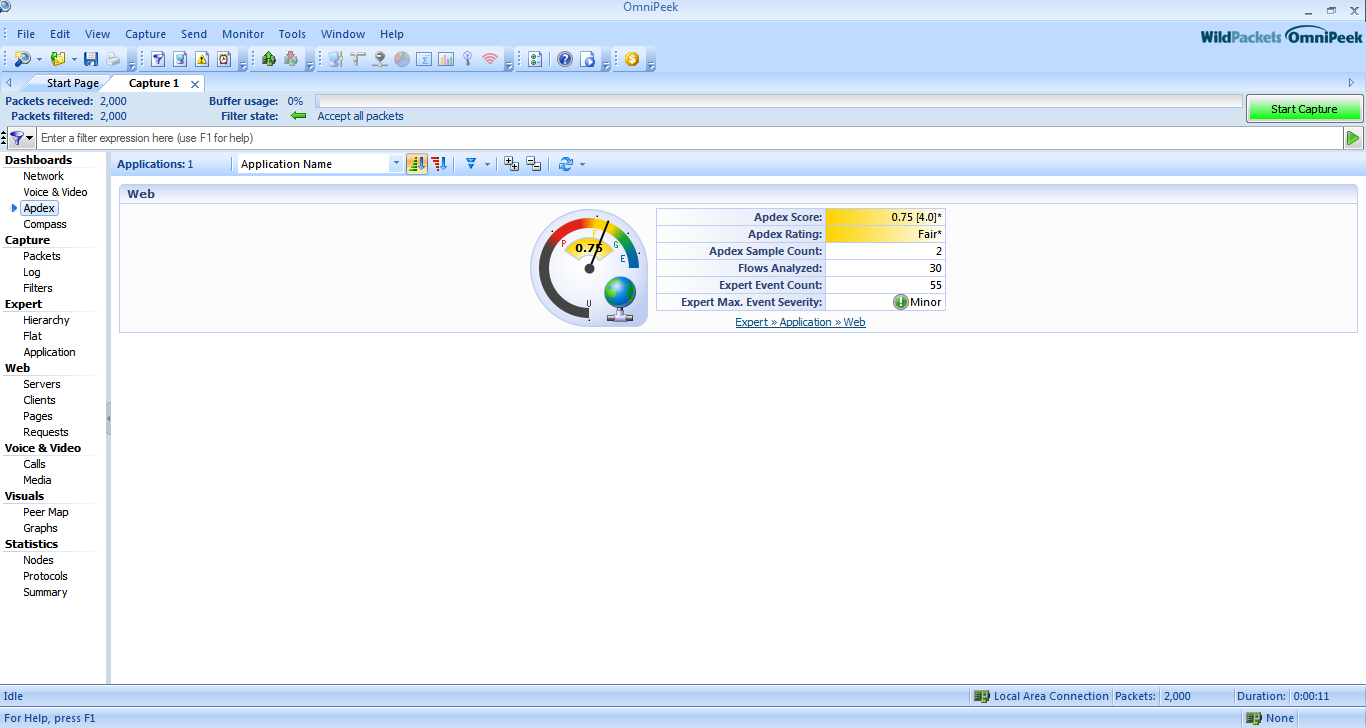 Log
Log
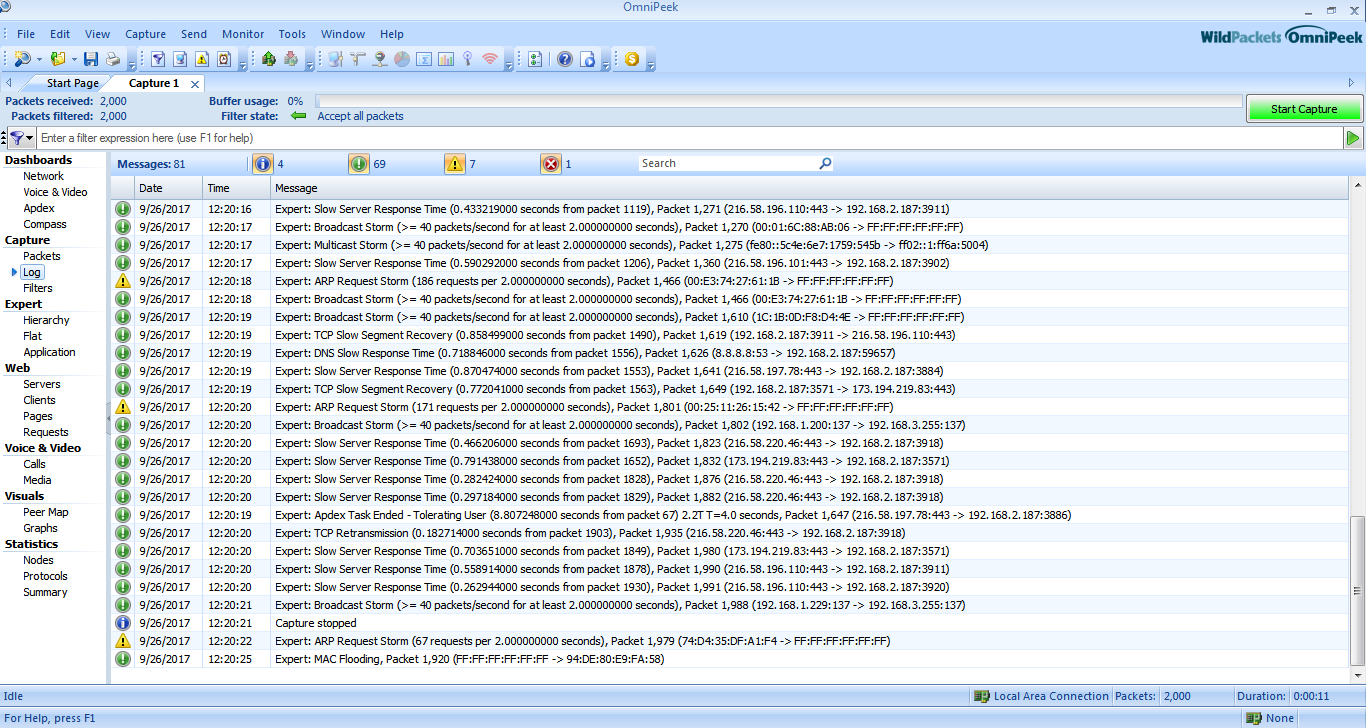 Filters
Filters
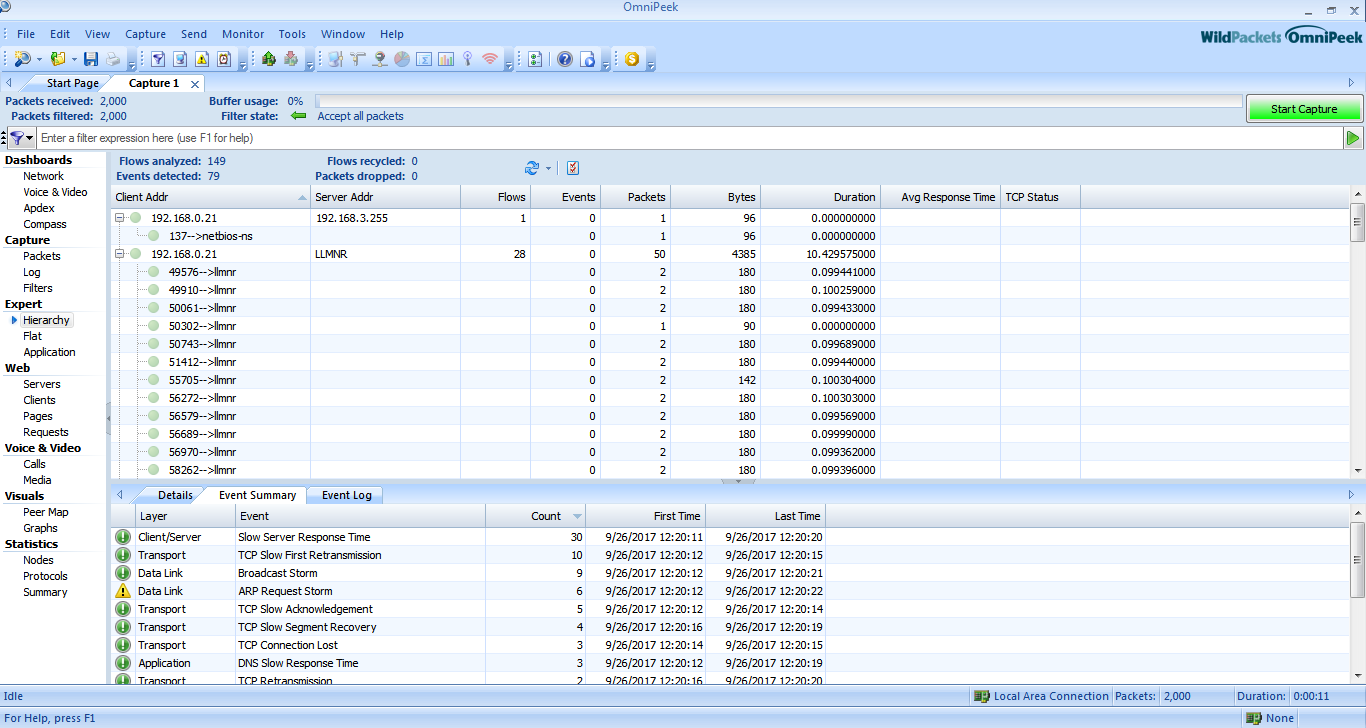
 Hierarchy
Hierarchy
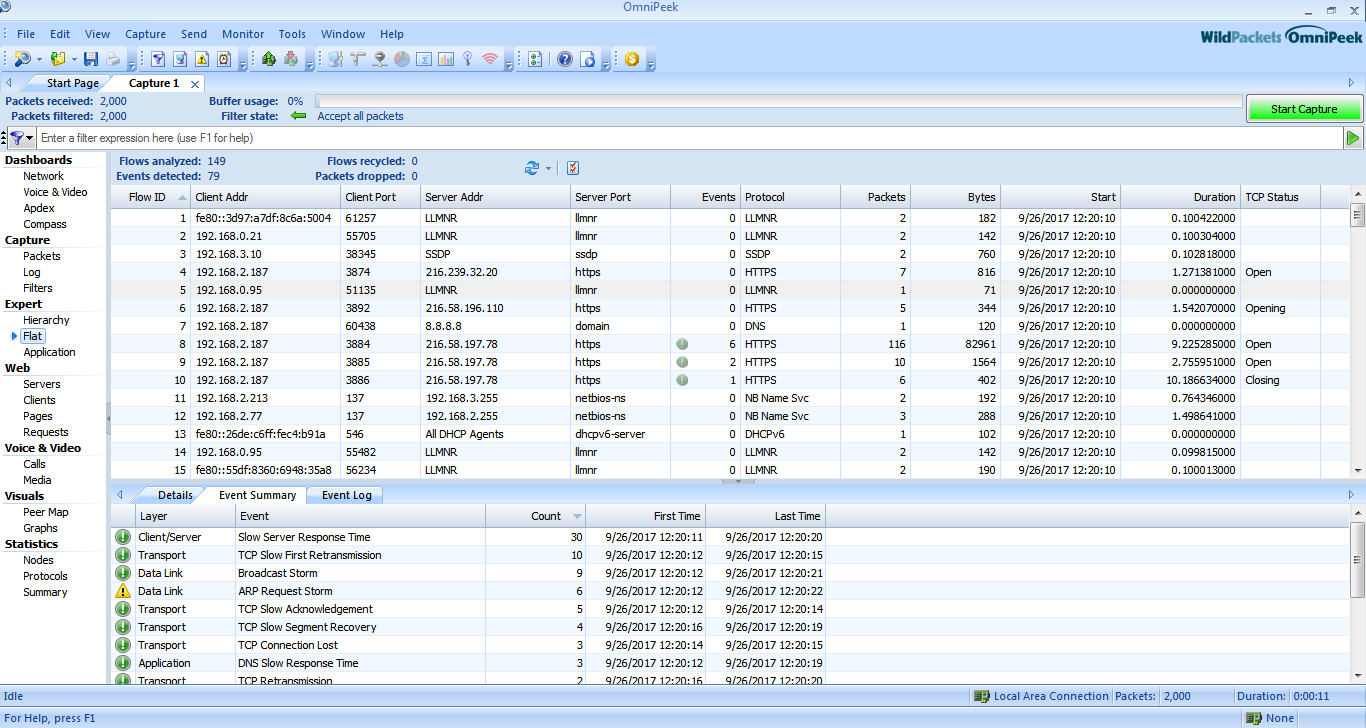
 Flat
Flat
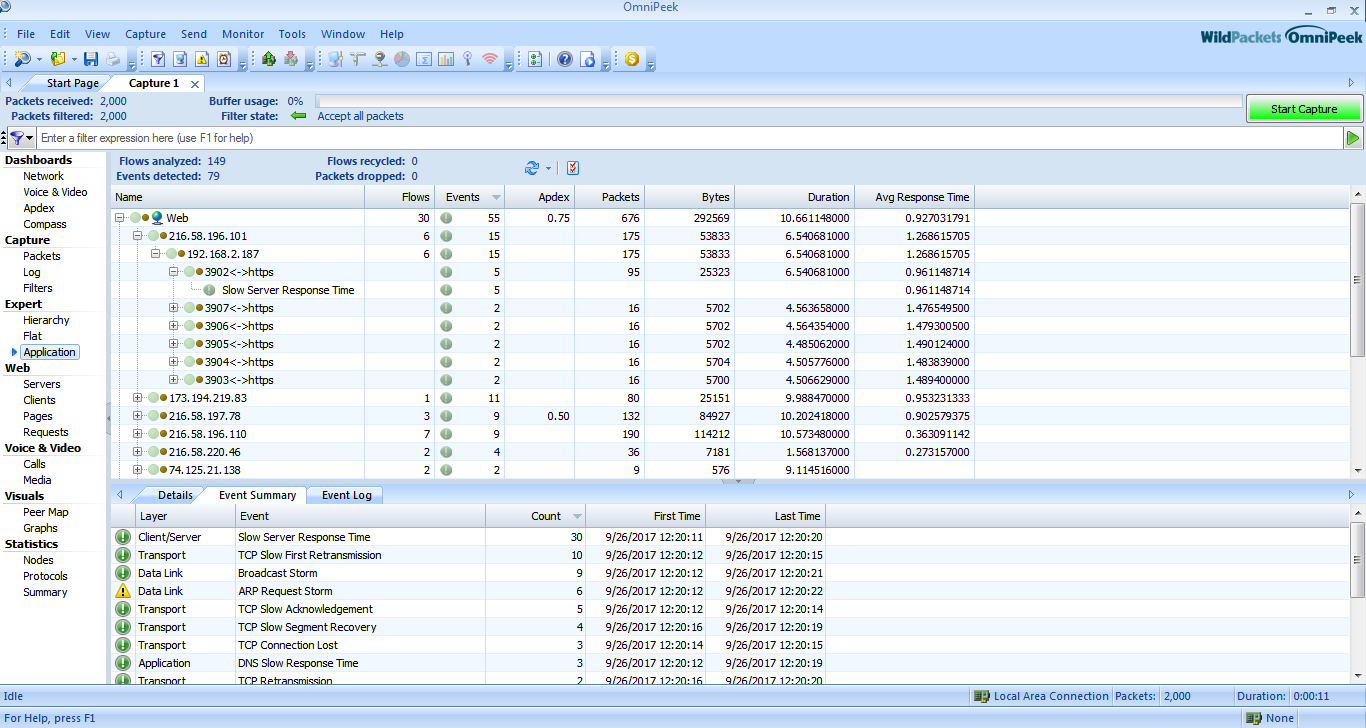
 Applications
Applications
 peer map
peer map
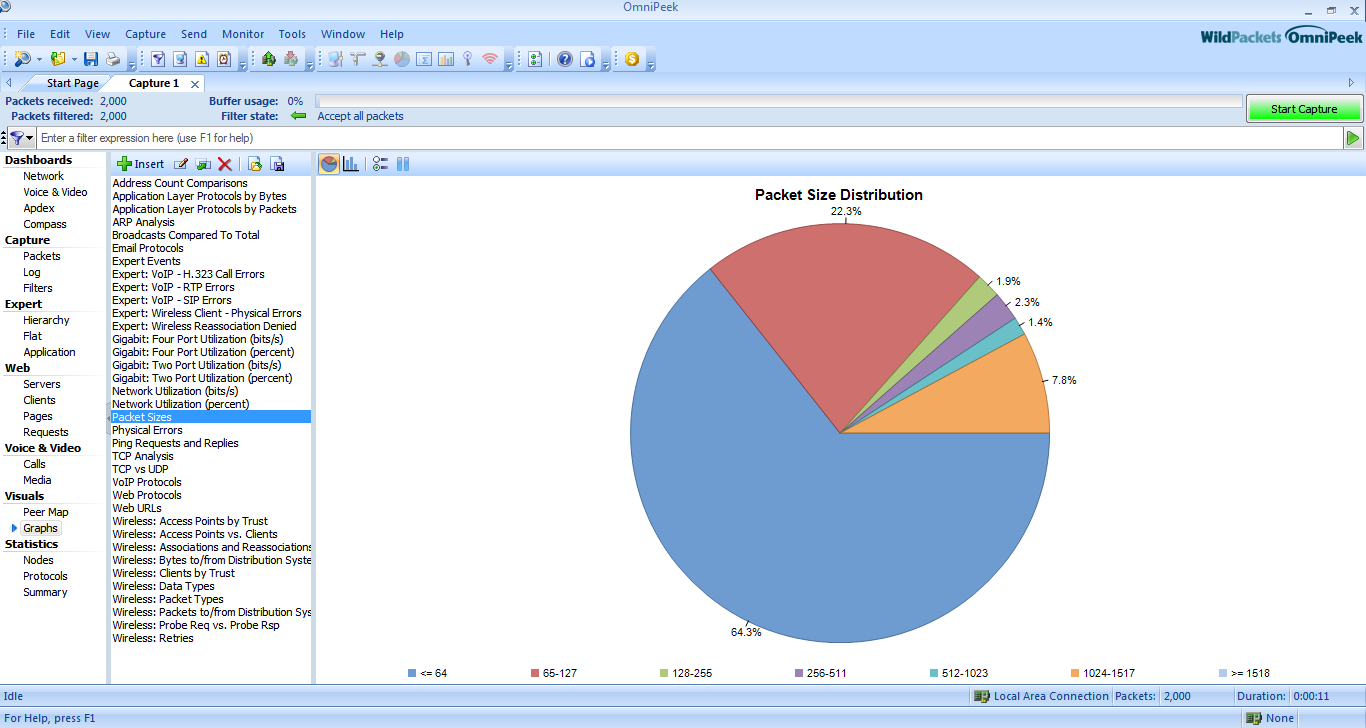
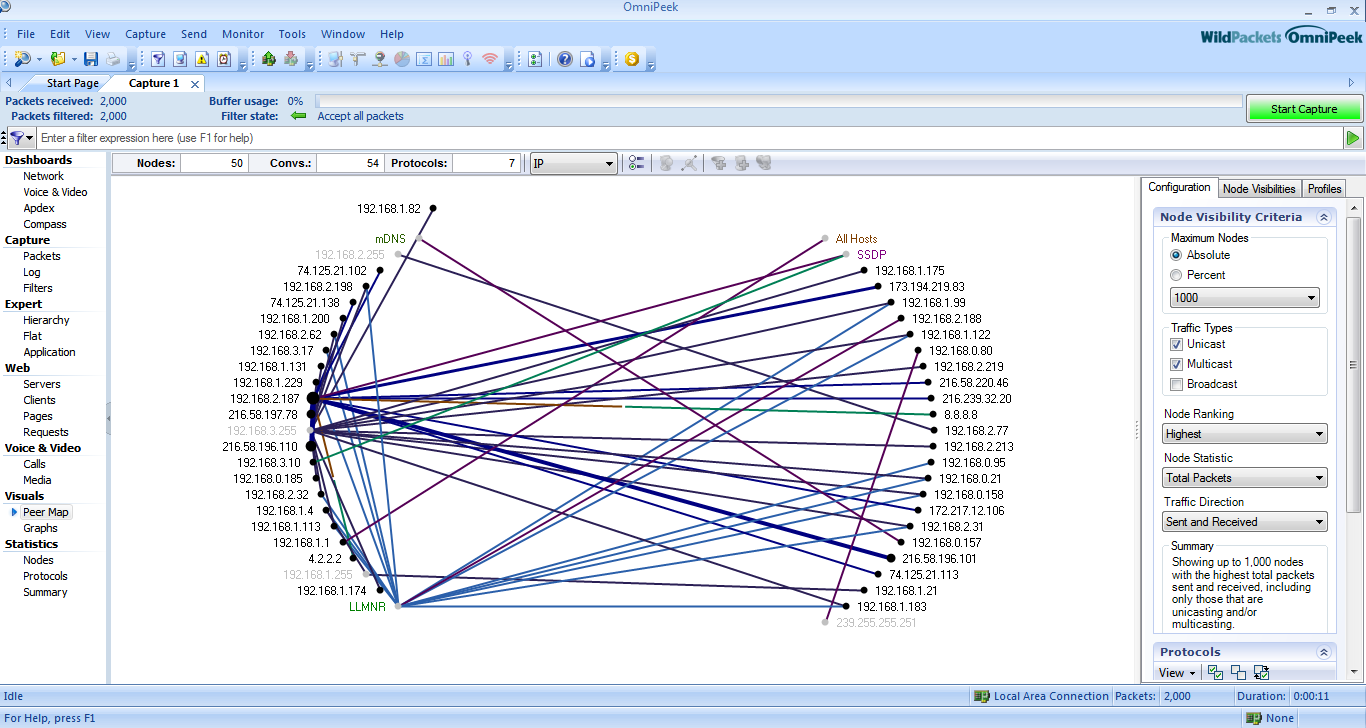 Graphics
Graphics
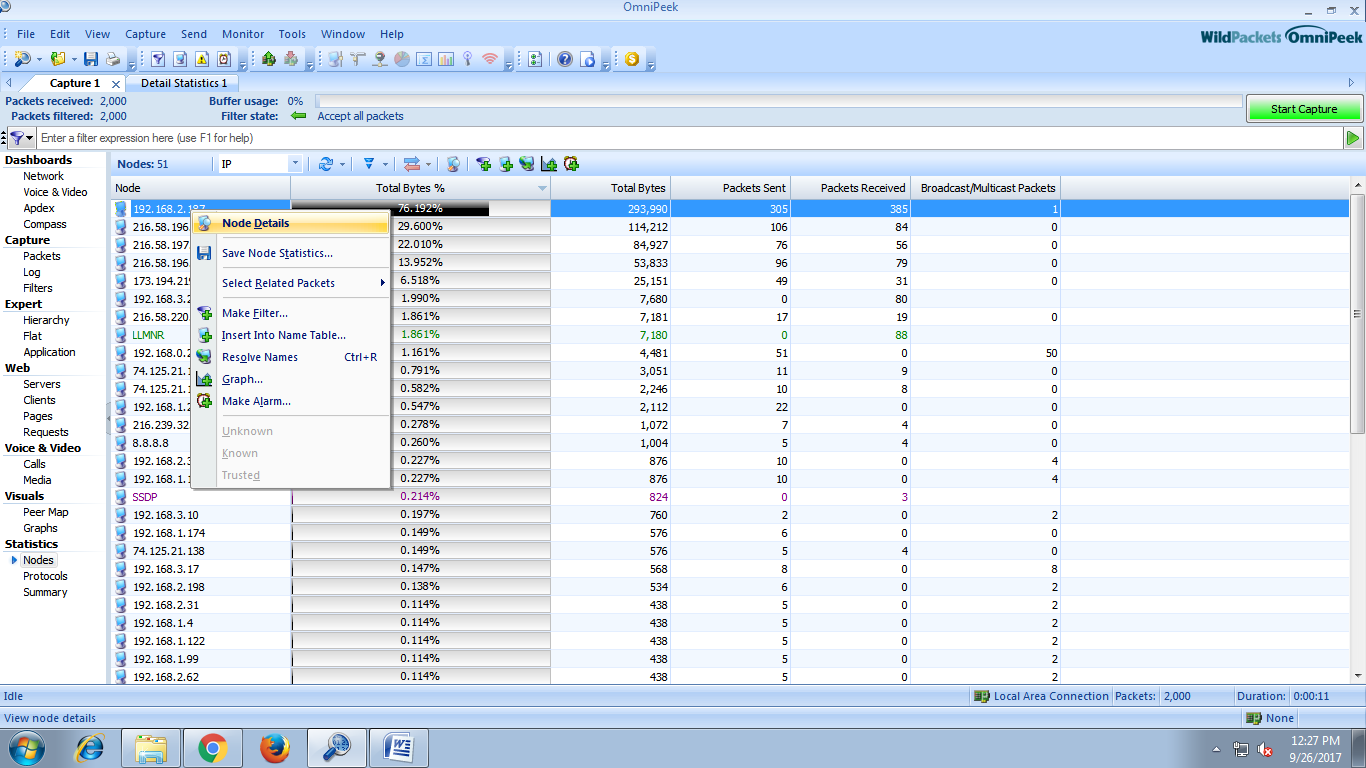
 Select IP --> Node Details
Select IP --> Node Details
 Details of IP address
Details of IP address
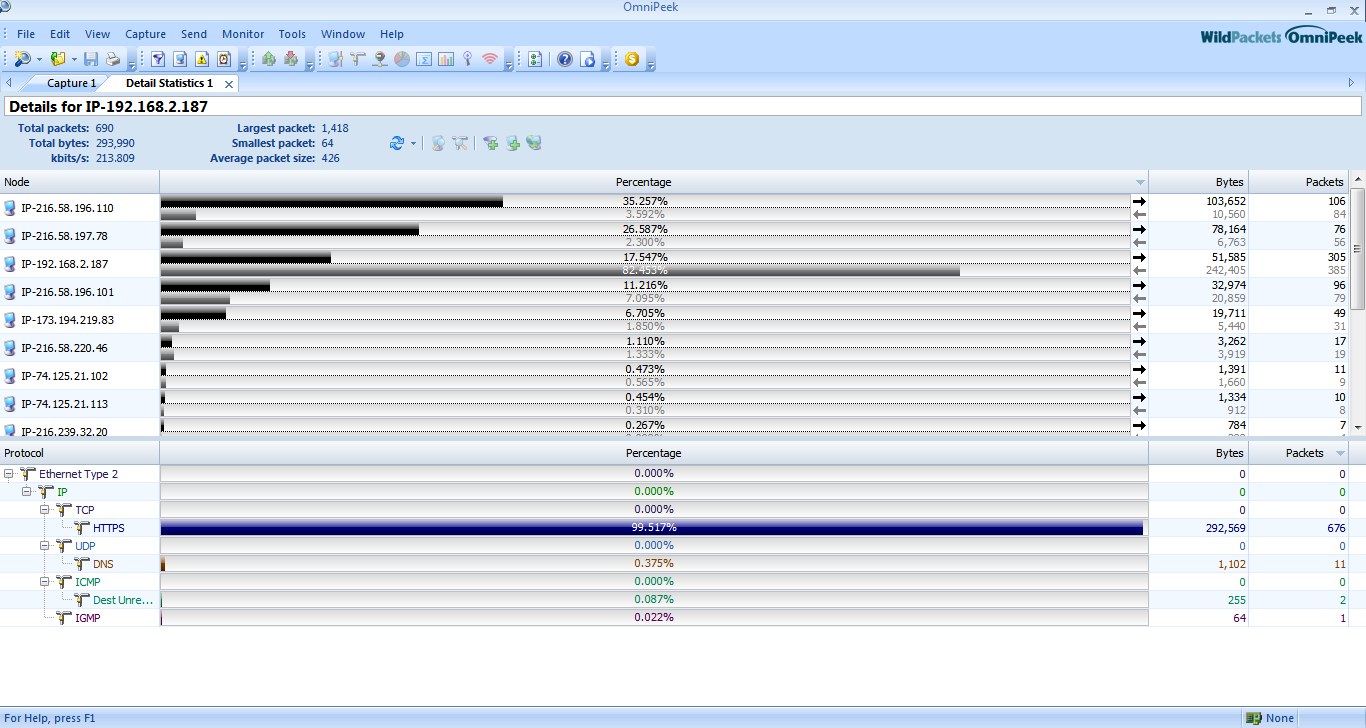 We can also know protocol used by the ip address.
We can also know protocol used by the ip address.
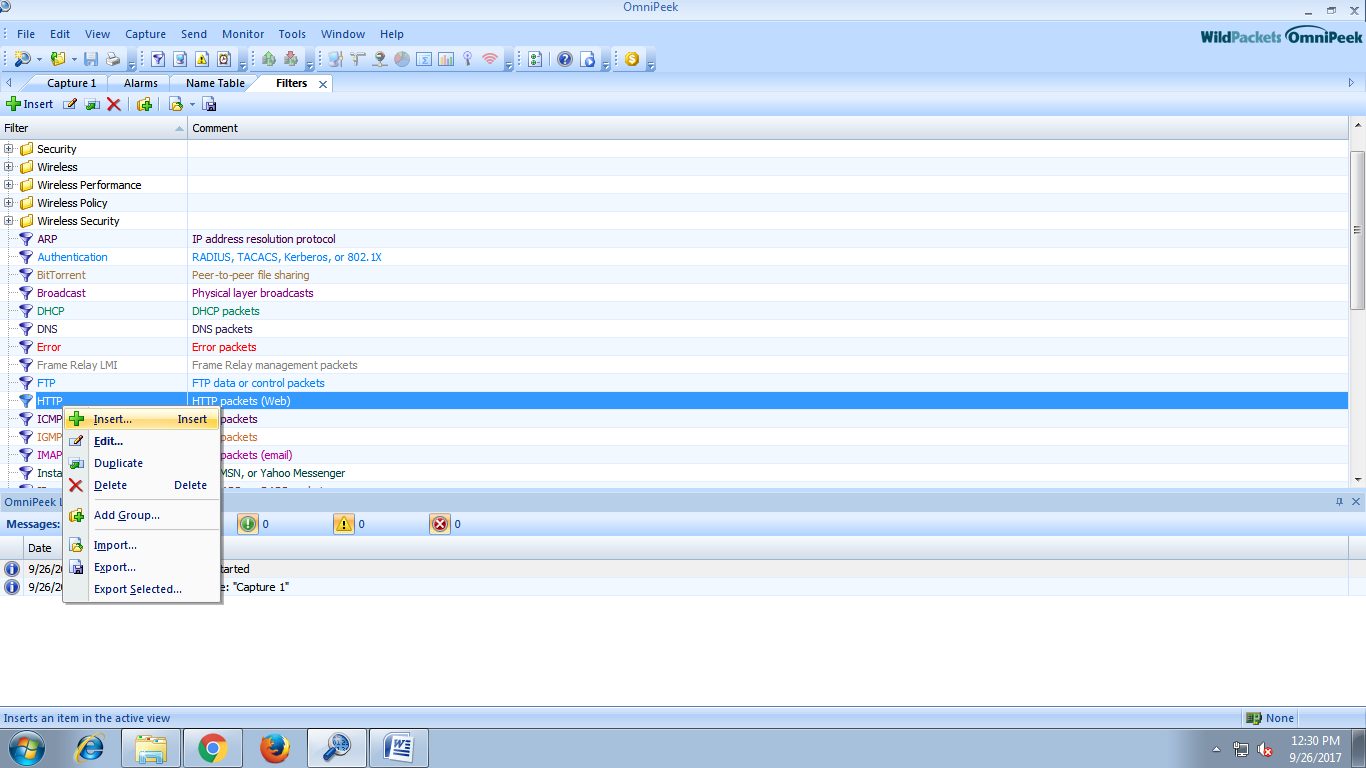
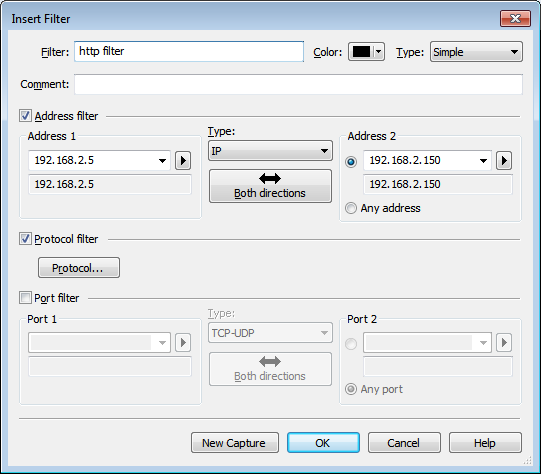
 We can filter the packet by inserting some new rule.
We can filter the packet by inserting some new rule.
 Click on new capture and click on start scanning
Click on new capture and click on start scanning
 Open Wire-shark or https://www.wireshark.org/download.html .
Open Wire-shark or https://www.wireshark.org/download.html .
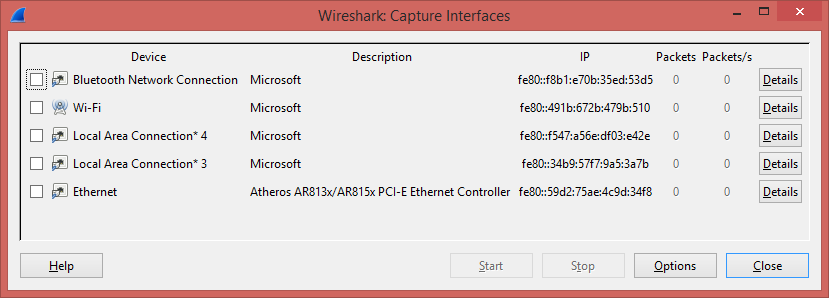
 Select Interface
Select Interface
 Start Scanning for Local Area Network Interface to capture packet.
Start Scanning for Local Area Network Interface to capture packet.
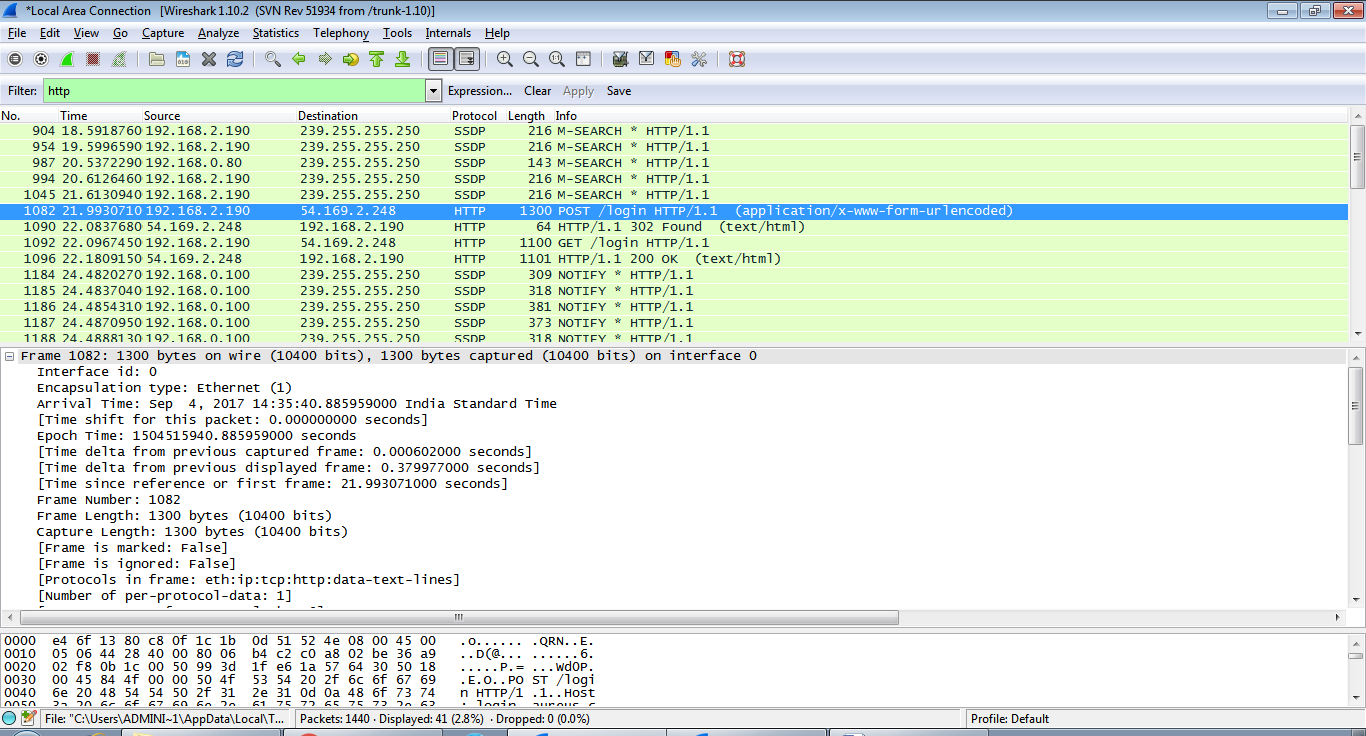 Filter HTTP Packet and look for GET and POST method.
Filter HTTP Packet and look for GET and POST method.
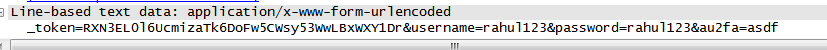
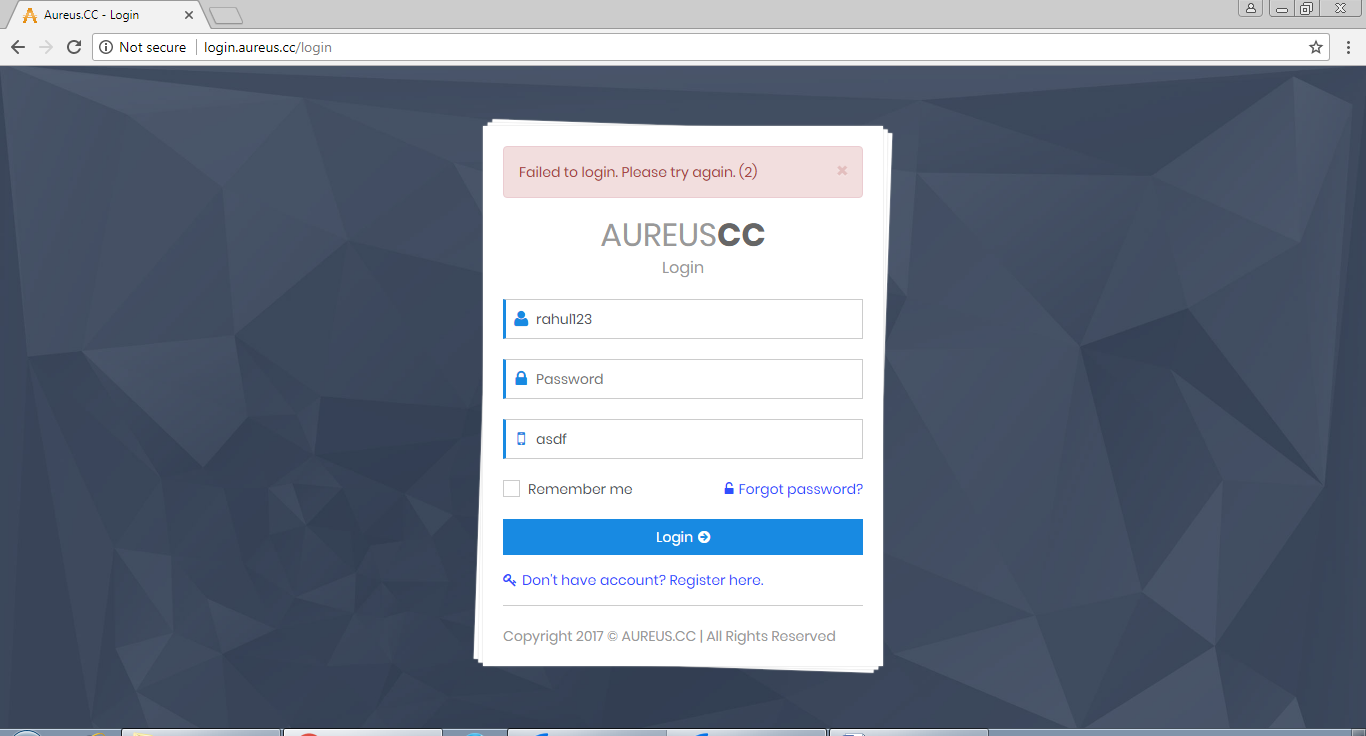
 Find Line-Based Text Data in GET and POST Packet of HTTP.
Find Line-Based Text Data in GET and POST Packet of HTTP.
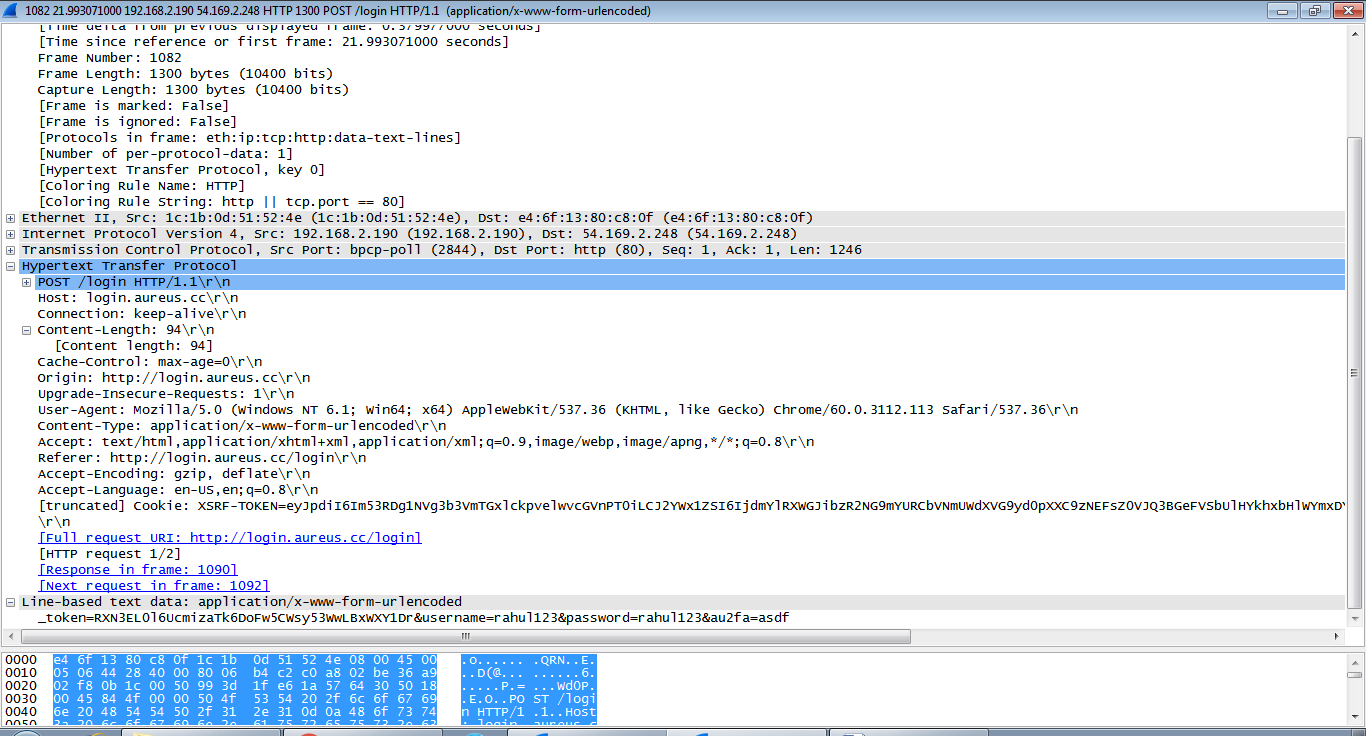 We can See User Id and Password in plain text.
We can See User Id and Password in plain text.