Self defence

Crypto tax evasion

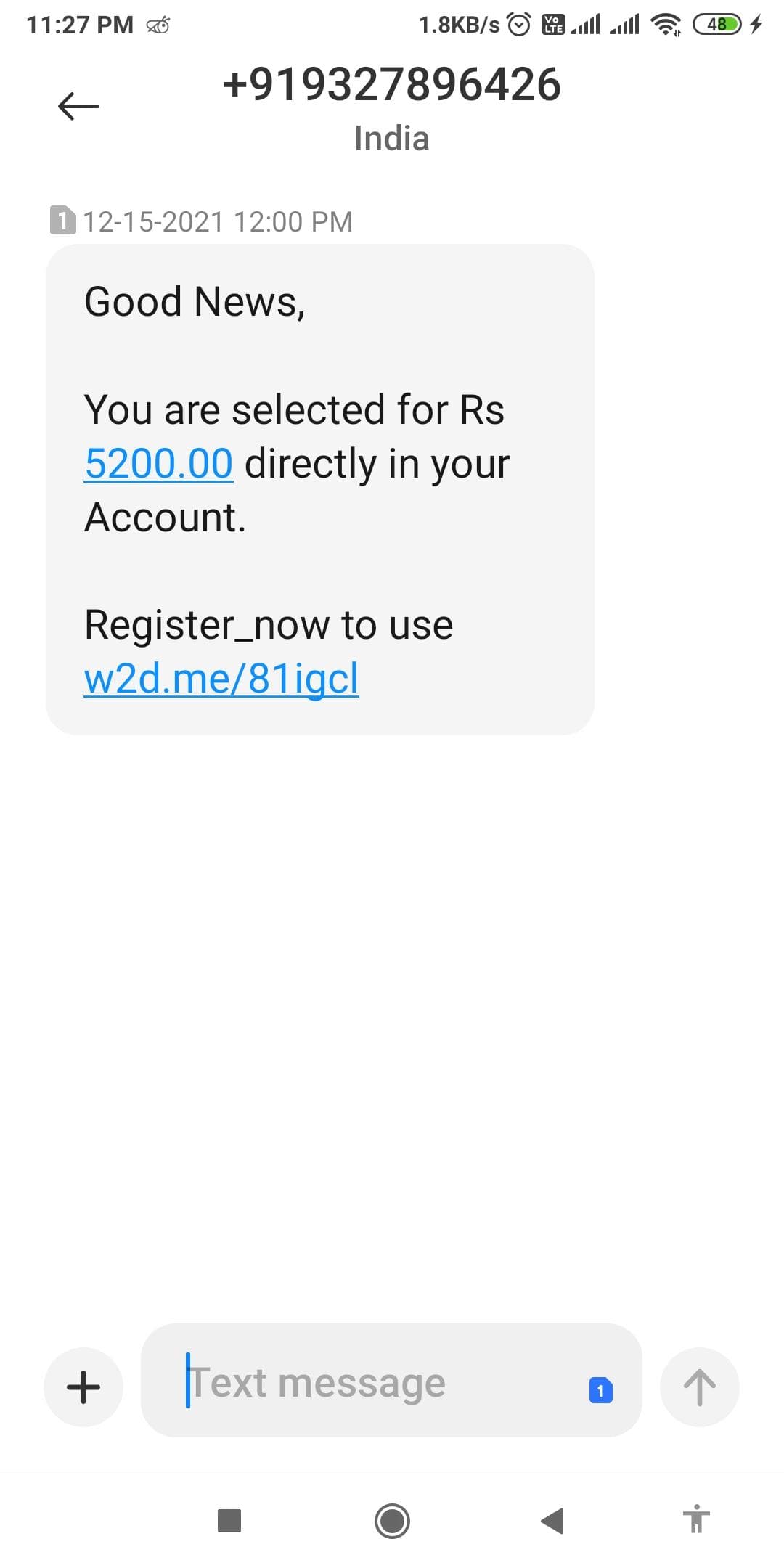
Different types of scam Fraud
DURGA POOJA
Linux Threads:
What do you mean by online marketing and why do you need to know about it

Service stratergy principles

QUANTUM COMPUTING IN SECURITY:A GAME CHANGER IN DIGITAL WORLD
Smartsheet

Blockchain

Hacking

Sensory Play for Toddlers: Boosting Curiosity Through Touch, Sound, and Colour

Smitten Kitchen Keepers

Security issues

Disk Management

MODERN OPERATING SYSTEM
Beatbox

Know your Processors!
Synchronization

Real time scheduling

Top 4 Places To Stay In Copenhagen

Old age lifestyle

Linker
Student Grade Calculator in LISP

Types of Viruses

History of ITIL

The Rich Heritage Of Patola Sarees: Gujarat’s Timeless Weaving Art

MoSCoW METHOD IN DATA SCIENCE
Water Resources are about to exhaust...

Image Steganalysis in Digital Forensics
Deadlock
Cache Memory(142)
APACHE KAFKA
Raid

IoT Architecture Based Security

Deadlock and Starvation
Virtual Memory - Explaination, Working, Steps
Deadlock
Use case of K-means clustering

Deadlock
Process, process creation and process termination
How I use google in my daily life