


A deadlock in an operating system is a situation where a set of processes become stuck because each process is waiting for a resource that another process holds. Since no process can proceed until the resource it needs becomes available, and the resources are all tied up, the system effectively "locks up.
Conditions for Deadlock
For a deadlock to occur, four conditions must hold simultaneously:
Mutual Exclusion: At least one resource must be held in a non-shareable mode; only one process can use the resource at a time.
Hold and Wait: A process holding at least one resource is waiting to acquire additional resources that are currently being held by other processes.
No Preemption: Resources cannot be forcibly removed from the processes holding them until the process voluntarily releases the resource.
Circular Wait: There must be a circular chain of processes where each process holds at least one resource and is waiting for a resource held by the next process in the chain.
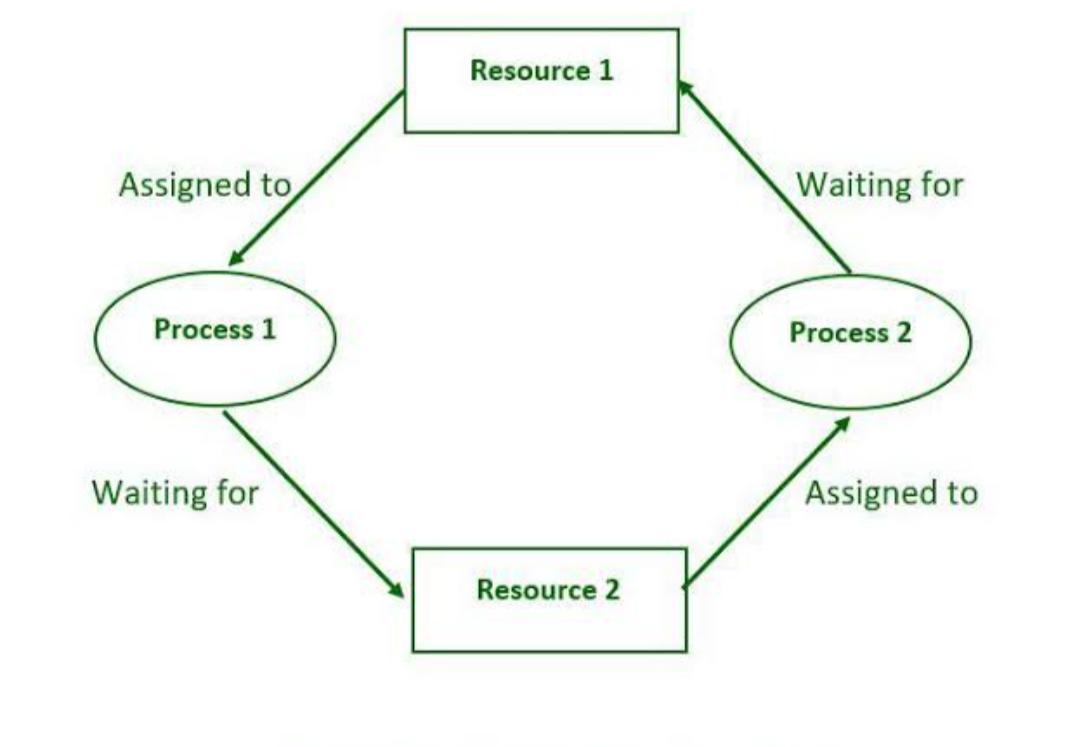
Example of Deadlock
Imagine two processes, P1 and P2, and two resources, R1 and R2
P1 holds R1 and is waiting to acquire R2.
P2 holds R2 and is waiting to acquire R1.