


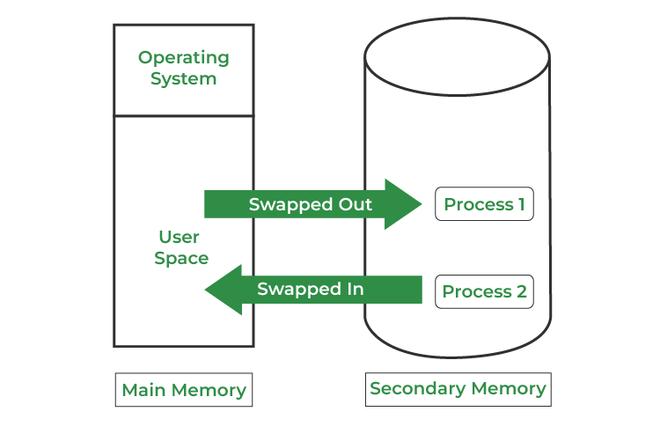
Memory management is a crucial aspect of operating system design that involves handling the allocation, management, and optimization of a computer’s primary memory. Effective memory management ensures that programs execute efficiently and securely, optimizing the use of available memory resources.
>> Memory Management Requirements
1. Relocation :
- Relocation refers to the process of assigning load addresses to different parts of a program and adjusting the code and data to reflect the assigned addresses. This enables a program to execute correctly regardless of where it is loaded in memory. Programs often use logical addresses which must be mapped to physical addresses.
2. Protection :
- Memory protection ensures that a program cannot accidentally or intentionally modify the code or data of another program. Mechanisms such as base and limit registers, segmentation, and paging are used to enforce protection.
3. Sharing :
- Memory sharing allows multiple processes to access the same physical memory locations. This saves memory space and facilitates inter-process communication. Shared libraries and shared memory segments are common mechanisms for implementing memory sharing.
4. Logical Organization :
- Logical organization refers to how programs are structured and how memory is organized from a programmer's perspective. This organization includes modules, which separate code and data into logical units, and sections, which divide programs into code, data, and stack segments.
5. Physical Organization :
- Physical organization deals with the actual layout of memory hardware and how data is physically stored. This includes RAM (Random Access Memory) for primary storage and cache memory for faster access to frequently used data.
>> Memory Partitioning
1. Fixed Partitioning :
- Fixed partitioning divides memory into fixed-sized regions or partitions. While simple to implement, it can lead to inefficient use of memory due to internal fragmentation.
2. Dynamic Partitioning :
- Dynamic partitioning creates memory partitions dynamically based on process needs, leading to more efficient use of memory with less fragmentation. However, it can result in external fragmentation over time.
3. Buddy System :
- The buddy system is a memory allocation scheme that divides memory into partitions to satisfy memory requests as suitably as possible. Memory is divided into blocks of size \(2^n\), and buddies of size \(2^{n-1}\) are combined to form larger blocks when needed. This reduces fragmentation and supports efficient allocation and deallocation.
4. Relocation :
- Relocation involves moving programs and data around in memory to optimize usage. Static relocation adjusts addresses at compile time, while dynamic relocation adjusts addresses at runtime.
>> Paging
Paging is a memory management scheme that eliminates the need for contiguous allocation of physical memory. Memory is divided into fixed-size pages, which are mapped to physical memory frames. This reduces fragmentation and simplifies memory allocation. Key components of paging include the page table, which maps virtual addresses to physical addresses, and the Translation Lookaside Buffer (TLB), a cache used to speed up address translation.
>> Segmentation
Segmentation divides a program's memory into variable-sized segments based on the logical divisions of the program, such as code, data, and stack. Segmentation reflects the logical structure of programs and supports protection and sharing but can lead to external fragmentation. A segment table maps segment numbers to physical addresses.
>> Security Issues
1. Buffer Overflow Attacks :
- Buffer overflow attacks occur when more data is written to a buffer than it can hold, overwriting adjacent memory. This can lead to arbitrary code execution, crashes, and security breaches.
2. Defending Against Buffer Overflows :
- Techniques to defend against buffer overflows include bounds checking to ensure data written to a buffer does not exceed its capacity, Data Execution Prevention (DEP) to prevent execution of code from non-executable memory regions, and Address Space Layout Randomization (ASLR) to randomize memory addresses, making it harder for attackers to predict the location of malicious code. Using safe programming languages and libraries that handle memory more safely also mitigates the risk of buffer overflows.