


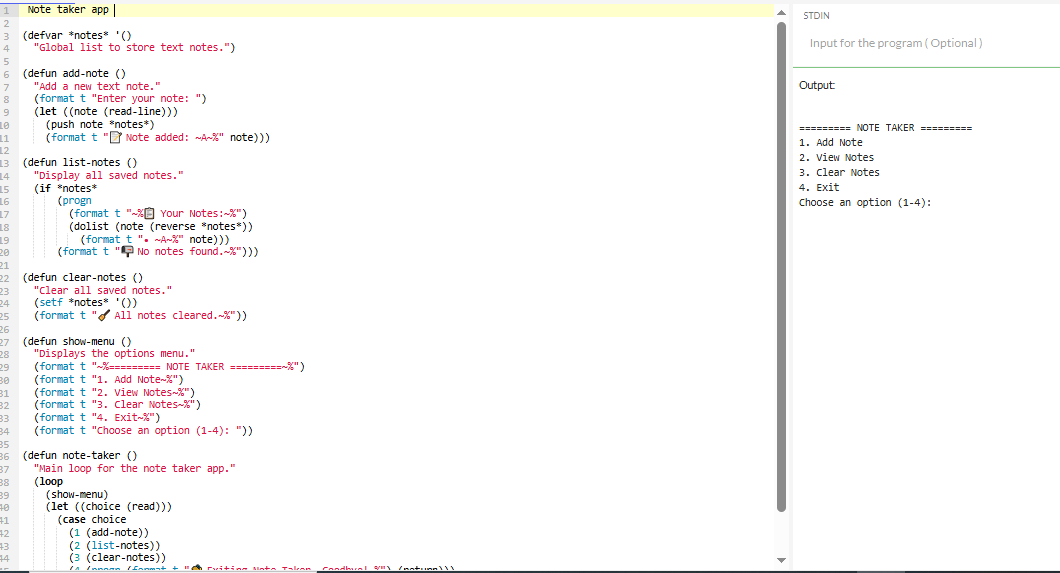
(defvar *notes* '()
"Global list to store text notes.")
(defun add-note ()
"Add a new text note."
(format t "Enter your note: ")
(let ((note (read-line)))
(push note *notes*)
(format t "📝 Note added: ~A~%" note)))
(defun list-notes ()
"Display all saved notes."
(if *notes*
(progn
(format t "~%📋 Your Notes:~%")
(dolist (note (reverse *notes*))
(format t "• ~A~%" note)))
(format t "📭 No notes found.~%")))
(defun clear-notes ()
"Clear all saved notes."
(setf *notes* '())
(format t "🧹 All notes cleared.~%"))
(defun show-menu ()
"Displays the options menu."
(format t "~%========= NOTE TAKER =========~%")
(format t "1. Add Note~%")
(format t "2. View Notes~%")
(format t "3. Clear Notes~%")
(format t "4. Exit~%")
(format t "Choose an option (1-4): "))
(defun note-taker ()
"Main loop for the note taker app."
(loop
(show-menu)
(let ((choice (read)))
(case choice
(1 (add-note))
(2 (list-notes))
(3 (clear-notes))
(4 (progn (format t "👋 Exiting Note Taker. Goodbye!~%") (return)))
(t (format t "❌ Invalid option. Try again.~%"))))))