



What are the different types of E-mail crime and process of email forensic?
10 Amazing facts about Tokyo Ghoul

Apache Kafka

Which Smartphone Company Has the Largest Market Share in India?
Dangers of Using Public WiFis

Rain bow

This Windows 11 encryption bug may cause data damage

I/O Buffering

Digital Marketing - The new way to reach end consumer
All you need to know about “Off-page SEO”
GIS Applications: How Different Industries are Leveraging Geospatial Data

PROCESS STATES OF OPERATING SYSTEM

Clustering Techniques
"Audit" In Data Science

The Rise of Evil Twin Attacks: A New Kind Of Spoofing Cyberattack

Excel records

What is semaphore in operating system?
GIS info about Bermuda Triangle
Article on IT development trends

Service Design Principles

Predicting Student Performance with Data Science

Zero Trust Security Model: Revolutionizing Cybersecurity in the Digital Age
indian premier league

Service transistion under difficult conditions

Data Visualization
Understanding Business Layer in Data Science
Data Visualization- Importance and tools (Tableau,Power BI, Matplotlib)

What is Spyware?

Article on Fresh Book

virtual machines and virtualization

Data is an asset and it is your responsibility!

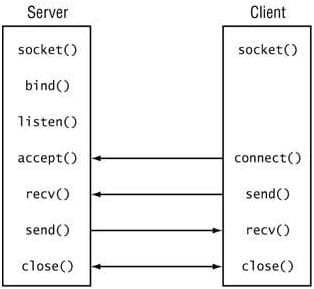
Practical Implementation of Client Server model using TCP/IP.
Interrupts in OS
Race Condition
Predictive Analysis - Ek Overview
Scheduling

Assignment-3
"The Benefits of Using GIS in Agriculture"
Threads and concurrency
How to lose belly fat

Advanced Persistent Threats (APTs)
File Systems in OS.
Direct Memory Access
