



You have have heard about the term "Salting" with respect to passwords.So what actually is salting? Does it improve the security of password? How does salting work? Lets find out!
So What is password Hashing and Salting?
A hash is just a way to represent any data as a unique string of characters.Hashing can use lengthy unique strings depending on the type of algorithm applied.Commonly used hash is Md5 which returns a 32 character hash.When you make an account on a website or app, the password you use must be saved so that you can be recognized the next time you visit. However, this password cannot be saved in plaintext, i.e without any formatting or coding. To prevent hackers from accessing your account, the password must be hashed.
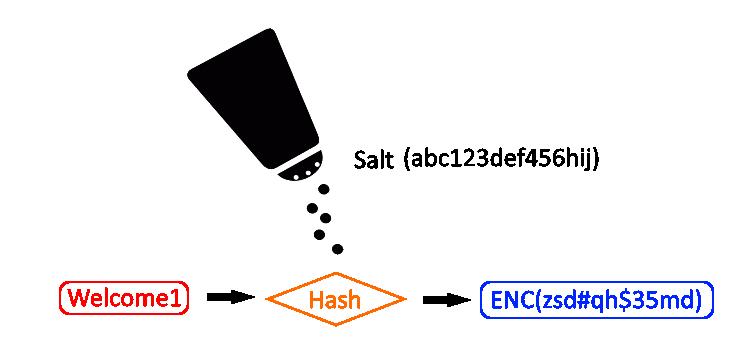
Salting is the process of adding unique random strings of characters to passwords before the password is hashed.These unique strings of characters that are added before or after the password is known as the "salt".This is done to change the hash and make the password more secure and hard to crack.Salting adds an extra degree of protection to hashing. To increase the security of a hash, unique sequences of characters are added to the password before hashing to modify the hash.
For example if you login to a website with the password: Password123. Before that password gets hashed, a salt value is added to it. Consider the alt value added to the password is AH#$1D, your salted password becomes Password123AH#$1D or AH#$1DPassword.This salted password is then hashed and stored in the database alongside other password hashes.
Suppose your orginal password is Password123 and its hash is 2f56eecd822cc9bd6ceb9f8990cc859d.
Adding salt ,makes the salted password as Password123AH#$1D and its hash to 914d738342254c4ea67e148719be5d89
As we can see the hashes are completely different. The password remains the same when you visit the site, but the hash is more secure against exploitation.Hash is usually very helpful if you have a weak password that can be cracked easily
What is the purpose of Salting these passwords?
Since hackers use techniques such as bruteforcing that use vast directories of words or numbers,It makes it easy for a hacker to guess the password using various permutations and combinations,especially if your password is a simple one or weak.Hackers also use RainbowTables which have terabyte of data that uses reverse engineering to guess passwords.Hence salt must be added to password which makes the use of Rainbow Tables useless.
To make passwords hashes unique
Salting is also important when two or more users have the same passwords. Adding different randomized salts to each password helps to make each unique