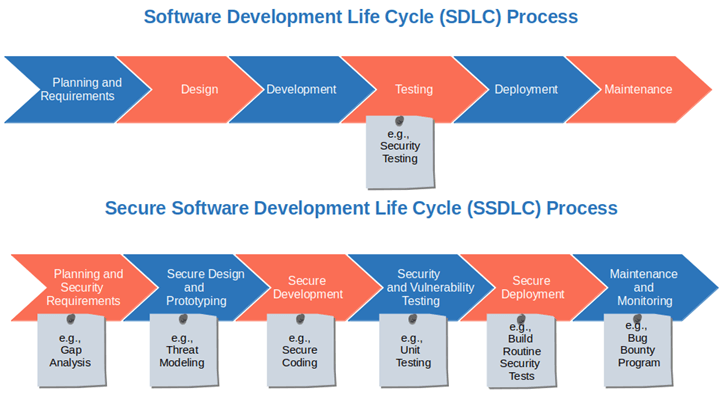
Understanding the Secure SDLC: -
The Secure SDLC is not an afterthought or a checklist but a philosophy. It acknowledges that security should be a guiding principle throughout the entire software development process. It encompasses the following essential phases:
1. Requirements Gathering and Analysis:
- Traditional SDLC begins with defining requirements. In the Secure SDLC, security requirements are explicitly identified. What are the security goals and constraints? What regulations must be adhered to?
2. Design:
- Security considerations are woven into the architecture and design of the software. This involves threat modeling to anticipate potential vulnerabilities and attacks.
3. Coding:
- Developers follow secure coding practices to write code that's resistant to common security threats like SQL injection, Cross-Site Scripting (XSS), and buffer overflows.
4. Testing:
- Security testing is integrated into the testing phase. This includes activities like vulnerability scanning, penetration testing, and code reviews to identify and rectify security issues.
5. Deployment:
- Secure configurations are applied during deployment, and access controls are fine-tuned. Security patches are kept up-to-date.
6. Monitoring and Maintenance:
- Continuous monitoring is essential to detect and respond to security incidents promptly. Regular maintenance includes applying security updates and patches.

The Benefits of Secure SDLC
1. Proactive Security:
- By making security a central part of the development process, you're addressing vulnerabilities as you go, rather than reacting to them later.
2. Cost Savings:
- Fixing security issues after deployment is significantly more expensive than addressing them during development.
3. Compliance:
- Secure SDLC helps organizations comply with various regulations and standards, such as GDPR or HIPAA.
4. Reputation Management:
- A security breach can severely damage an organization's reputation. Secure SDLC minimizes the risk of such breaches.
5. Time Efficiency:
- Contrary to the belief that security slows down development, integrating it into the SDLC can speed up the process by reducing rework and costly post-release fixes.
6. Resilience:
- Secure SDLC ensures that your software is resilient to emerging threats and vulnerabilities.
Challenges and Considerations
Implementing Secure SDLC is not without its challenges. It requires buy-in from all stakeholders, ongoing training, and a cultural shift towards prioritizing security. Moreover, balancing security with other project constraints, such as time and budget, can be tricky.
Conclusion
In the digital age, security is not a feature; it's a necessity. The Secure SDLC provides a framework for creating software that is not only functional but also robust and resilient against a constantly evolving threat landscape. By embracing security as an integral part of your software development process, you're not only protecting your organization's assets but also building trust with your users and stakeholders. In a world where breaches and cyberattacks are becoming increasingly prevalent, the Secure SDLC is your blueprint for building a digital fortress that stands strong against the relentless tide of cyber threats.





