


What is a Session?
A session is a series of interactions that take place within a single connection between two communication endpoints. A web application does not require authentication for every click since, HTTP is stateless, which means designers need to automate tracking the state of multiple connections from the same user. When a user logs into an application, a session is created on the server to ensure subsequent requests are synchronized.
The application uses sessions to keep track of parameters that are unique to the user. As long as the logged-in user remains, the session is kept “alive” on the server. After a certain period of inactivity, a session is destroyed immediately upon the user logging out of the system. Data belonging to the user should be deleted from the allocated memory space whenever a session terminates.
An attacker hijacks a user session to gain control over it. A session starts when you log in and out of a service, like your bank’s application. A cookie hijack or cookie side-jacking is an attack that relies on an attacker knowing your session cookie. Session hijacking is commonly associated with web browsers and web applications, yet it can happen with any application.
Session hijacking and spoofing are closely related, but the timing of their attacks differs. Session hijacking occurs when an attacker hijacks a user’s login and authentication credentials. And from the victim’s point of view, it often results in unpredictability or crashes of the targeted application.
When spoofing occurs, attackers use stolen or counterfeit tokens to initiate a new session that appears to be set by the original user.
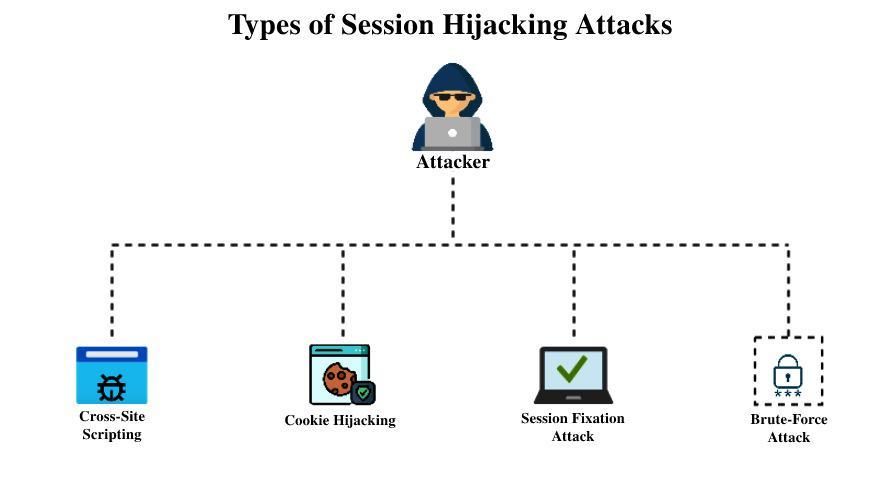
To hijack a user’s session, an attacker can use several techniques, depending on the attacker’s position. Examples of session hijack attacks include:
When an attacker exploits vulnerabilities within a server or application, he injects Java scripts into a user’s web page, causing the browser to run arbitrary code. Moreover, injected scripts will be able to access your session key if the server does not set HTTP. Only in session cookies, thus, giving attackers the information required for session hijacking.
An attacker can intercept the session cookies of a user after he or she authenticates them by using packet sniffing. By using SSL/TLS only for its login pages, the website takes the easy route and the attacker can steal the session key and impersonate the user to operate the web application.
Generally, this happens with an unsecured WiFi Hotspot, as the attacker can access the network, monitor the traffic, and then set up their access points to conduct the attack.
Using a session key, attackers gain access to the server by spoofing the user’s credentials. Due to stateless protocols, there is a threat of session hijacking. It is these limitations that make the protocols vulnerable to attacks.
An SSL connection uses Secure Sockets Layers, which protect any personal information required to pass between the two systems. Thus, it reduces the risk of criminals reading and modifying the messages sent over the internet. Transport Layer Security (TLS) is simply an updated, more secure version of SSL.
After the attacker has gained access, they can perform any actions authorized by the original user while the session is active. If the targeted application involves financial theft, the attacker may demand ransom to release data from the encrypted form, steal the users’ sensitive personal information from company systems, or steal money directly from their bank account.
In large organizations, cookies may be used to identify authenticated users within SingleSign-on (SSO) Systems. An attacker who successfully hijacks a session can gain access to various web applications, from financial databases and customer records to line-of-business applications containing valuable intellectual property.
When you log in using your Facebook account, or Google account, there are more safeguards in place, meaning that hijacking a session cookie won’t be enough to hijack your session.
Sessions are attacks that exploit data leaks in TLS request compression ratios. The attackers could then use the login cookies to hijack the user’s session. An organization known as CRIME used session hijackers to breach an organization’s website in September 2012.
After hijacking the website’s session by decrypting HTTPS cookies and logging in as users with brute force, CRIME was able to siphon off an enormous amount of data.