



The password is a critical element of information security. Let's take a look at some of the best techniques to crack passwords and protect your own.

What is Password Cracking?
Password cracking is the process of guessing or recovering passwords from data that has been stored in a computer system. In most cases, this is done by using a tool that tries to guess passwords based on common patterns.
If a hacker has access to a user's login information (such as an email address and password), they may try to use a technique called credential stuffing to log in to multiple websites with the same credentials in order to find one that works.
No matter what technique is used, password cracking can be a time-consuming process. However, it is often worth the effort for hackers because gaining access to sensitive information can be very valuable.
Types of Passwords:-
There are three types of passwords: Those that can be easily guessed, those that can be easily cracked, and those that are strong. The best password cracking technique depends on the type of password you're trying to crack.
If you're trying to crack a password that's been encrypted, the best techniques vary depending on the encryption algorithm used. However, in general, brute-force attacks are the most effective. This involves trying every possible combination of characters until the correct password is found.
If you're looking for a strong password that will be difficult to crack, the best advice is to use a combination of letters, numbers, and special characters. The longer the password, the better. A good rule of thumb is to create a password that's at least eight characters long.
Different Techniques for Password Cracking:-

There are a few different techniques that can be used for password cracking. The most common technique is called brute force, which involves trying every possible combination of characters until the correct password is found. This can be very time-consuming, so other methods have been developed to try and speed up the process.

The another popular technique is dictionary attacks, which involve trying common words and phrases that might be used as passwords. This method can be quite effective, but it obviously won’t work if the password isn’t a common one.
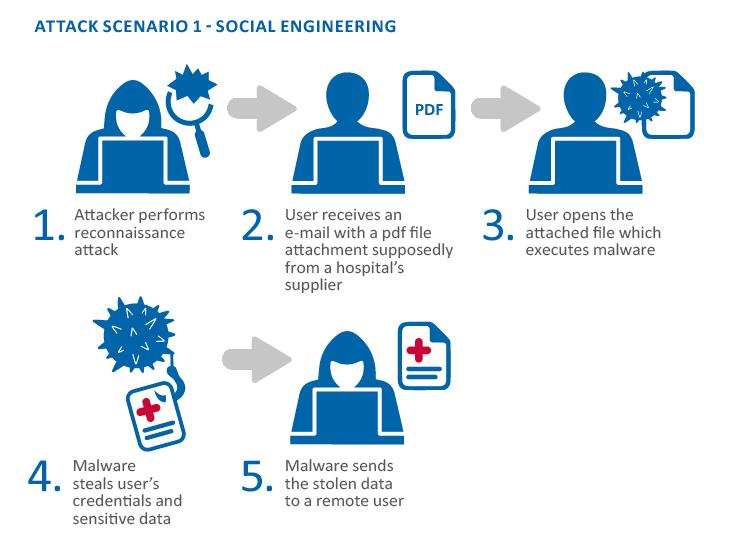
The other approach that is sometimes used is known as “social engineering attack”. This involves trying to trick people into revealing their passwords, either through deception or by exploiting human weaknesses such as greed or vanity. This technique can be surprisingly effective, but it obviously carries a higher risk of getting caught.
Tips for Password Cracking:-
If you're looking to crack a password, there are a few techniques you can try. The most common and effective method is brute force, which involves trying every possible combination of characters until you find the right one. This can be time-consuming, but it's often the only way to crack a difficult password.
Another technique is to use a dictionary attack, which involves trying common words and phrases until you find the right one. This is usually faster than brute force, but it's less likely to be successful on complex passwords.
Finally, you can try a social engineering attack, which involves tricking someone into revealing their password. This is the most difficult method to pull off, but it can be very effective if done correctly.
Conclusion:-
There is no one-size-fits-all answer to this question, as the best password cracking technique will vary depending on the situation. However, some of the most popular methods include brute force attacks, dictionary attacks, and rainbow table attacks. If you're not sure which technique is best for your needs, be sure to consult with a professional before proceeding.