


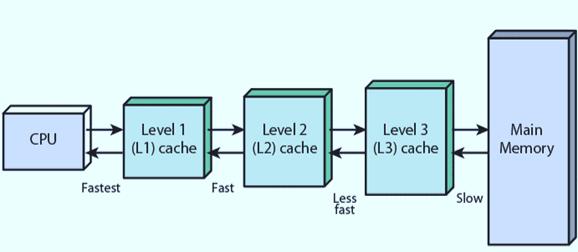
Cache memory is basically a kind of random access memory (RAM) which is inbuilt in processor. The cache memory is used to built a bridge of speed gap between the fast CPU and slow RAM therefore it improves overall performance of the computer.
There are 2 parts of cache memory:
1) Inbuilt cache processor
Level 1: Level 1 cache memory is the smallest in size but the fast among all four. It is located inside the processor. It is separated into instructions cache (L1i) and data cache (L1d). Every core has its own dedicate L1 cache
Level 2: level 2 cache memory is a little bigger size than level 1. It is also slow as compare to Level 1. It is dedicate to one single core or shared between multiple core.
Level 3: level 3 cache memory has bigger size than level 2 but is faster than level 2. It is dedicated to multiple core only.
2) Advanced Cache Configurations
Level 4: level 4 is not inbuilt but it must be close to processor to perform its best. It is used when high performance task. Not all computers have level 4 cache memory.
Advantages of cache memory:
1) High Speed access: Cache memory is faster than RAM because it's frequently access data and instructions rather than being idle.
2)improvement in Performance: Cache memory improves performance by minimising the average time of access data.
3)High Speed: nowadays processor is so fast that RAM could not provide data at right time. To overcome this problem cache memory sync the ram and processor
Disadvantage of cache memory:
1) Cost: The cost to make cache memory is more expensive than RAM due to technology and materials used to achieve such high speed and low latency
2) Complexity: design of cache memory is very complex. All levels require different design.
3)Security: cache memory can be attacked with the help of certain types of side channel attacks. This provides the hacker to use and manipulate our sensitive data.