


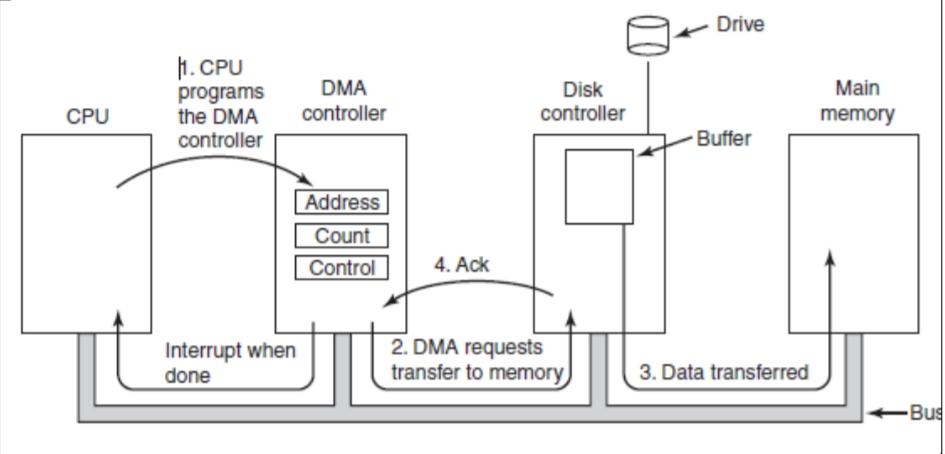
DMA permits data transfer directly between I/O device and main memory,
without involvement by the CPU.
• The transfer of data is first initiated by the CPU.
• During the data transfer, the CPU performs other tasks. When the data
transfer is completed, the CPU receives an interrupt request from the DMA
controller.
• The operating system can use only DMA if the hardware has a DMA
controller.
• Consider a data transferred from disk drive to main memory with DMA as
shown in fig.
Steps-
1. CPU initiates data transfer by programming DMA controller’s registers.
Control- transfer data from disk to main memory
Count- n Number of bytes to transfer
Address- Starting address location in main memory
2. DMA controller then requests disk controller to add data byte to be
transferred from the disk to its buffer.
3. The disk controller then sends the 1 data byte from buffer to the specified
memory location in main memory.
4. When the write is complete, the disk controller sends an acknowledgement
signal to the DMA controller. DMA controller then increments the address
value by 1 (next empty location to write the data) and decrements the byte
count value by one (1 byte is sent out of n bytes). Then steps 2,3,4 are
repeated till the count reaches 0.
5. When count=0, the DMA controller interrupts the CPU to let it know that
the transfer is now complete.