Malware, or malicious software, is any program or file that is intentionally harmful to a computer, network or server.Malware can infect networks and devices and is designed to harm those devices, networks and/or their users in some way.Depending on the type of malware and its goal, this harm may present itself differently to the user or endpoint. In some cases, the effect malware has is relatively mild and benign, and in others, it can be disastrous.No matter the method, all types of malware are designed to exploit devices at the expense of the user and to the benefit of the hacker -- the person who has designed and/or deployed the malware.
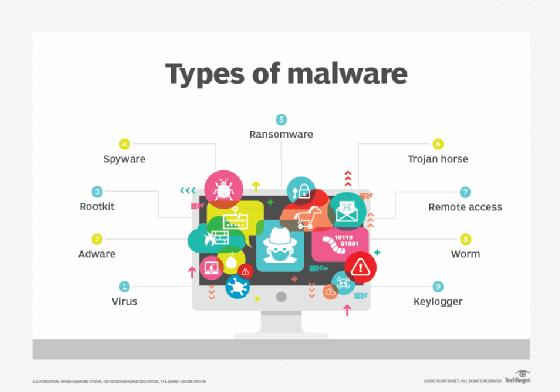
Types of malware include computer viruses, worms, Trojan horses, ransomware and spyware. These malicious programs steal, encrypt and delete sensitive data; alter or hijack core computing functions and monitor end users' computer activity.