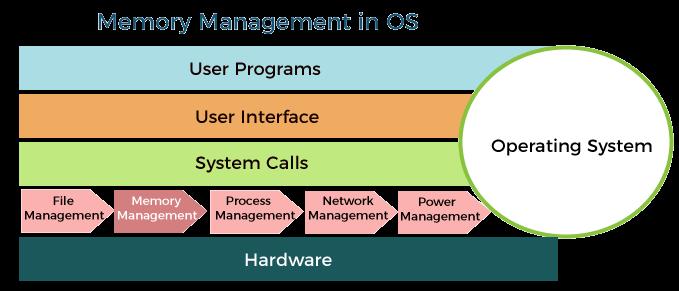
What is Memory Management?
Memory management refers to the system of controlling and coordinating laptop memory, assigning blocks to numerous running packages to optimize usual device overall performance. It guarantees that each technique has enough reminiscence to execute and that the system runs successfully.
Features :
Process Isolation:
- The running system (OS) ought to make sure that each program walking on a laptop doesn’t interfere with some other program's information or commands.
Example: Imagine you are running a web browser and a phrase processor on the equal time. The OS makes positive that the internet browser can not trade the record you are writing in the word processor and vice versa
Automatic Allocation and Management:
- The OS mechanically manages and allocates reminiscence to applications as needed with out bothering the programmer about reminiscence limitations.
Example: When you open a couple of applications, like a song participant and a sport, the OS allocates memory to each utility dynamically with a purpose to run easily with out you having to manipulate the memory manually.
Support of Modular Programming:
- Programmers can create software elements (modules), and they are able to effortlessly add, do away with, or resize these components even as this system is strolling.
Example: If you are growing a software program utility and also you want to feature a brand new function or dispose of an vintage one, you could accomplish that dynamically with out preventing the complete software.
Protection and Access Control:
- The OS guarantees that while reminiscence can be shared between programs whilst wanted, it also protects applications from unauthorized get entry to to their memory.
Example: If your laptop has consumer accounts for one of a kind family individuals, the OS guarantees that one family member’s packages and statistics are blanketed from get right of entry to with the aid of some other member of the family until sharing is explicitly allowed.
Long-term Storage:
- Some applications need to save statistics even if the pc is grew to become off, and the OS provides methods to store this records permanently.
Example: When you store a report in your word processor, the file is saved to your tough drive or SSD so that you can get admission to it once more even once you restart your computer.
Div - A
Chirag varu
Sap ID: 53003230110