Email System:-An email system, or electronic mail system, is a fundamental communication tool that enables the exchange of messages and files between individuals or groups over the internet.
Component of Email System:-An email system comprises serveral components that work together to facilitate the sending, recieving,and management of emails. The basic components of an email system are :-
- User Agent :- User Agent in the context of email generally refers to the email client or software that the sender used to compose and send the email.
- Mail server(Mail Transfer Agent):- A mail server is a computerized system that handles the sending, receiving, and storage of email messages.
- Mailbox(Mail Delivery Agent):- A mailbox refers to a location or storage space where email messages are stored for a particular user.
- SMTP server :- A Simple Mail Transfer Protocol server is a computer program or application that is responsible for sending and relaying outgoing email messages.
- Email Protocols:- Email protocols are sets of rules and conventions that define how email clients and servers communicate and handle the exchange of email messages.
Structure of Email:-The structure of an email is composed of several key elements that work together to convey information effectively.
- Header :- The header of an email contains metadata and routing information that provides details about the email's journey from the sender to the recipient.
- Subject:- The subject of an email is a brief description or title that provides recipients with an overview of the email's content or purpose.
- Body:- The body of an email is the main content that the sender communicates to the recipient.
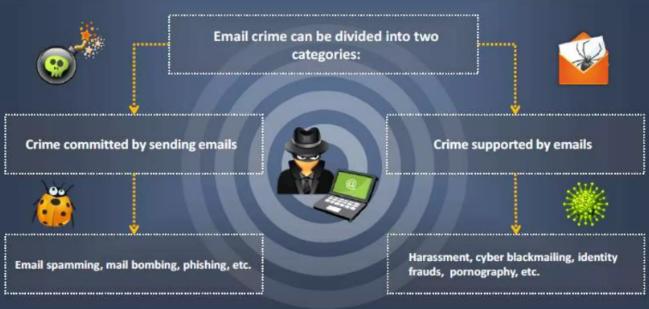
Email Crimes:-Email crimes encompass a range of illicit activities carried out through the use of email systems. These crimes often exploit vulnerabilities in communication protocols and attempt to deceive, defraud, or harm individuals, organizations, or systems. Some common email crimes include:
- Phishing:-Phishing emails are designed to trick recipients into revealing sensitive information, such as usernames, passwords, or financial details.Common tactics include posing as a trusted entity, like a bank or government agency, and creating fake websites or forms.
- Spoofing:-Email spoofing involves forging the sender's address to deceive recipients about the origin of the message.Spoofed emails may trick individuals into taking certain actions or believing false information.
- Spam:-Spam emails are unsolicited and often irrelevant or inappropriate messages sent in bulk.Apart from being a nuisance, spam can also be used to distribute malware or phishing attempts.
- Email Scams:-Various scams use email as a medium to deceive individuals, such as lottery scams, romance scams, or job offer scams.These scams often request money or personal information from the victim.
- Email Harassment and Threats:Some individuals use email to harass or threaten others. This can include hate speech, cyberbullying, or extortion attempts.Legal consequences may follow in cases of serious threats.
- Email Account Hacking:-Unauthorized access to email accounts can lead to identity theft, unauthorized access to sensitive information, or the use of the compromised account to launch further attacks.
Investigating Email Crime and Violation:-Investigating email crimes and tracking emails typically involve a combination of technical and legal approaches. Here are some general steps and considerations involved in tracking and investigating email crimes
- Obtain a Search Warrent : Legal authorization is crucial for conducting email forensics. Law enforcement or authorized personnel should obtain a search warrant from a court, demonstrating probable cause for the search.
- Obtain a bit-by-bit Email Information : Create a forensic image of the email storage media to preserve the original data. This ensures that the forensic analysis is conducted on a copy, preserving the integrity of the original evidence.
- Examine Email Header : Analyze the email header for valuable information. The email header contains details about the sender, recipient, timestamps, and the email's route through the network.
- Analyze Email Header :Examine the email content for any relevant information, including attachments, embedded images, and links.
- Track Email Origin : Use the information from the email header and other metadata to trace the origin of the email. This may involve identifying IP addresses, server logs, and other technical details that help determine where the email originated.
- Acquire Email Archives : Obtain access to email archives, if available. Email archives may contain historical data, deleted emails, and other information that is not present in the current mailbox.
- Recover Deleted Emails : Utilize specialized forensic tools and techniques to recover deleted emails. Deleted emails may still exist in the storage media until they are overwritten by new data.
Email Forencics Tools:-Email forensics involves the use of specialized tools to investigate and analyze email-related incidents for legal and investigative purposes. Here are some commonly used email forensics tools
- EnCase Forensic: EnCase is a widely used digital forensics tool that can be applied to analyze emails and other digital evidence. It provides features for disk imaging, data recovery, and email analysis.
- AccessData Forensic Toolkit (FTK): FTK is another comprehensive digital forensics tool that aids in the analysis of various types of digital evidence, including emails. It supports multiple email formats and can recover deleted emails.
- MailXaminer: MailXaminer is a specialized tool designed for email forensics. It supports the analysis of various email formats, attachments, and metadata. It is useful for investigations involving email-related crimes.
- MailParser: MailParser is a tool designed to extract data from emails automatically. It can parse and organize information such as email addresses, attachments, and timestamps, making it useful for forensic analysis.
- MBOX Viewer: MBOX Viewer is a tool that allows investigators to view the contents of MBOX files, a common format for storing email messages. It can be helpful in examining email archives.
Conclusion:-Email tracking for security purposes is valuable, it is protect from different email crime & violation. A comprehensive and collaborative approach involving IT professionals, legal experts, and law enforcement is essential for a successful investigation into email crimes.