


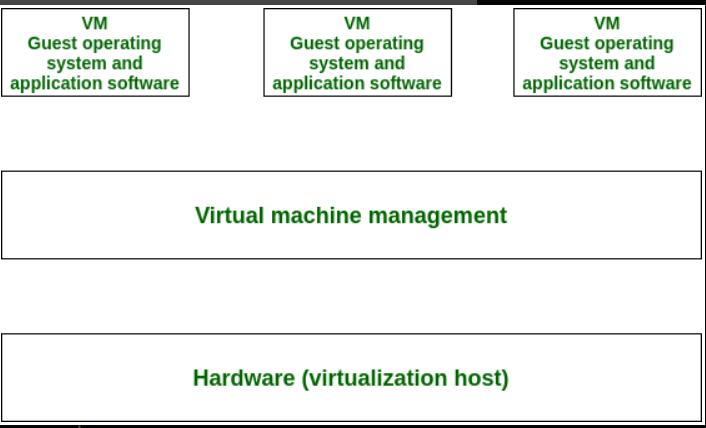
Operating system-based Virtualization refers to an operating system feature in which the kernel enables the existence of various isolated user-space instances. The installation of virtualization software also refers to Operating system-based virtualization. It is installed over a pre-existing operating system and that operating system is called the host operating system.
In this virtualization, a user installs the virtualization software in the operating system of his system like any other program and utilizes this application to operate and generate various virtual machines. Here, the virtualization software allows direct access to any of the created virtual machines to the user. As the host OS can provide hardware devices with the mandatory support, operating system virtualization may affect compatibility issues of hardware even when the hardware driver is not allocated to the virtualization software.
Virtualization software is able to convert hardware IT resources that require unique software for operation into virtualized IT resources. As the host OS is a complete operating system in itself, many OS-based services are available as organizational management and administration tools can be utilized for the virtualization host management.
Various major operations of Operating System Based Virtualization are described below:
1.Hardware capabilities can be employed, such as the network connection and CPU.
2.Connected peripherals with which it can interact, such as a webcam, printer, keyboard, or Scanners.
3.Data that can be read or written, such as files, folders, and network shares.