


System performance and stability may be affected by starvation and deadlock, which are two critical concerns in operating systems.
Starvation occurs when a process is continually refused the resources it needs to execute. Resource allocation policies often lead to this situation where some processes are favored over others. For example, low-priority processes may starve if high-priority processes perpetually demand and receive resources in a priority-based scheduling algorithm. This may result in resource utilization that is unfair and inefficient.
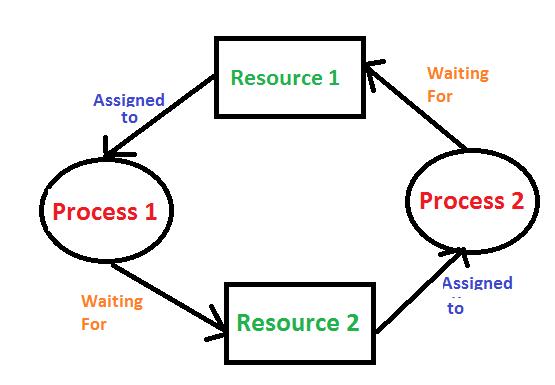
Conversely, deadlock is the state of affairs whereby two or more processes are unable to proceed with their execution since they are each waiting for a resource held by another process from the same set. This results into circular dependency: Process A waits for a resource that Process B holds while at the same time Process B waits for a resource that Process A holds. Deadlock can destroy an entire system as it could make processes hang indefinitely if not properly managed.
There are various strategies that can be employed to mitigate both starvation and deadlock:
Starvation: Fairness policies should be established so as to guarantee all the processes equal opportunities to access resources. In this regard, techniques such as aging can increase priority of processes that have been waiting for long thus reducing chances of starvation.