


IT risk management is the application of risk management method to information technology in order to manage IT risk. i.e the business risk associated with the use, ownership , operation, involvement, influences,and adaptation of IT within in enterprise or organisation.
IT risk can be considered the components of a wider enterprises risk management system.
The established , maintenance and continuous update of an information security management system ( ISMS) provide a strong indication that a company is using a systematic approach for the identification, assessment, and management of information security risk.
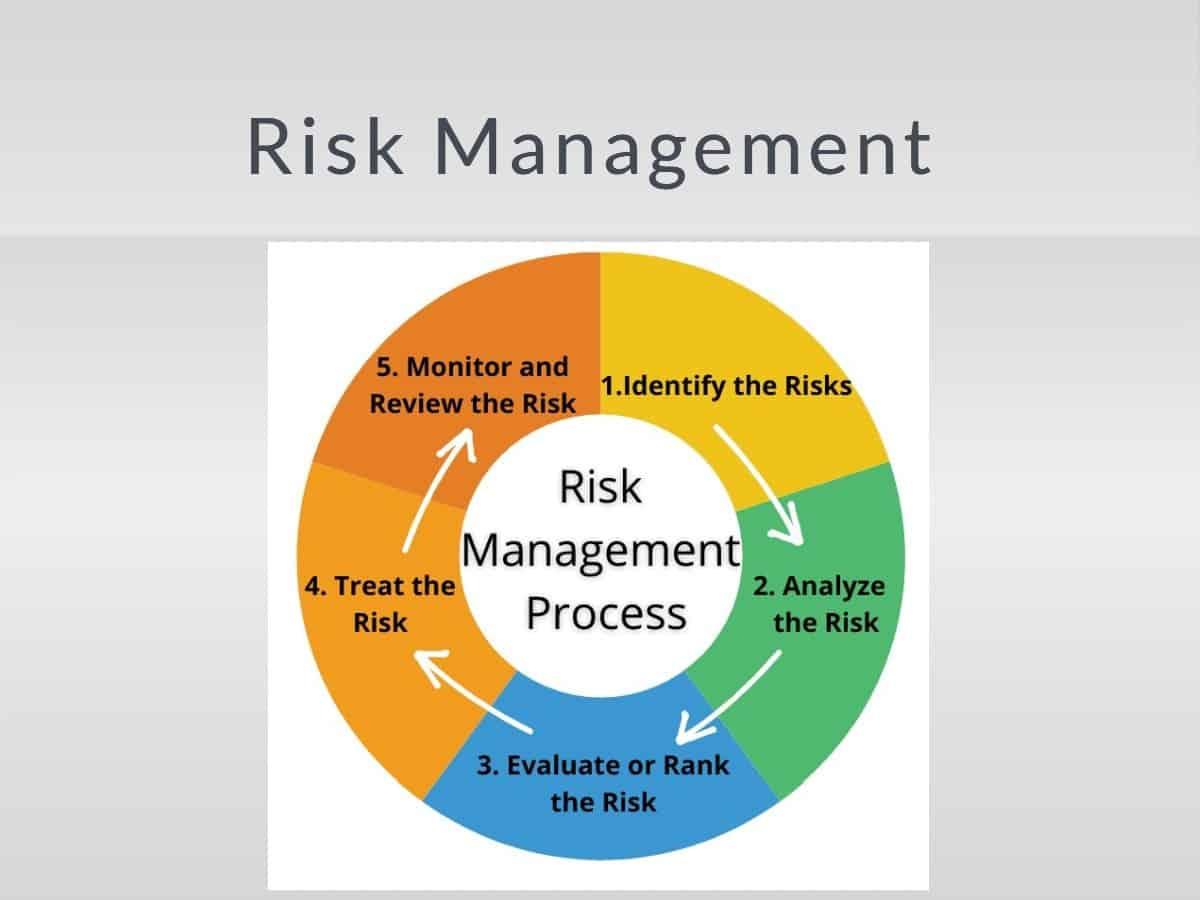
Different methodology has been proposed to manage IT risk and ecah of them is divided into process or steps.
IT risk management is the application of risk management method to information technology to manage the risk inherent in the space.To do that means assessing the business risk associated with the use, operation, ownership and adoption of the IT in an organisation. Because risk is strictly tied to uncertainty in the business operation,decision Theroy should be applied to manage the risk as a science i,e rationality, making choices under uncertainty.
Risk is a critical criteria in the management of the Organisation is should be managed equivalently and appropriately in order to run the organisation smoothly and efficiently.