


In an operating system (OS), a **session** generally refers to the period of time when a user or a process is actively using the system. Sessions are essential for managing user interactions, processes, and resources efficiently. Below are a few different types of sessions and their significance:
### 1. **User Sessions**
- A user session begins when a user logs into the system and ends when they log out. During this session, the OS maintains all processes, user files, and settings related to the user’s activity.
- Each user session typically has its own environment, including file permissions, access rights, and running applications.
### 2. **Terminal/Console Sessions**
- In systems like Linux or Unix, terminal sessions are created when a user opens a terminal or console. Each terminal session can run commands independently, with its own process ID (PID).
- **TTY (Teletype Terminal)** sessions: Text-based input/output streams, often seen in Unix-like operating systems.
- **PTY (Pseudo Terminal)** sessions: Used for creating terminal emulation, often by software like SSH.
### 3. **Network Sessions**
- Network sessions manage connections between a client and a server. These sessions are crucial in handling data transmission, ensuring proper communication between systems.
### 4. **Session Management in Windowing Systems**
- In graphical desktop environments (like GNOME, KDE), a session includes not only the user’s login state but also all open windows, running applications, and system preferences.
- These sessions may allow users to restore the desktop environment to the previous state upon re-login.
### 5. **Session Management in Web/Network Applications**
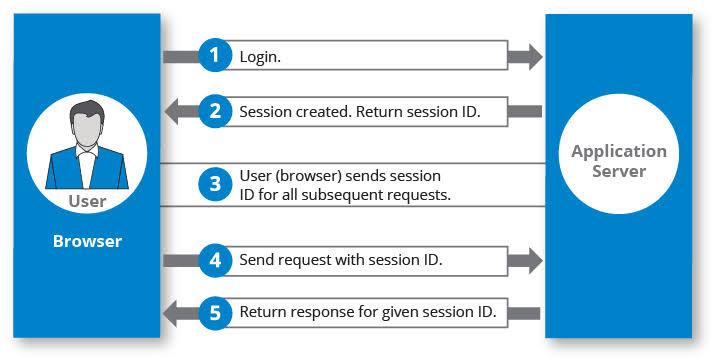
- Web applications create **sessions** to manage user state over stateless HTTP. A session in web terms might involve tracking user activities, login status, preferences, and shopping cart items.
- Sessions are managed using cookies or session tokens, which allow web servers to recognize consecutive requests from the same user.
### 6. **Process Sessions**
- In Unix-like operating systems, a session is a collection of one or more processes created by a single login.
- Processes in the same session share the same session ID (SID). A session leader (usually a shell) can create new processes within the session.
- Sessions are typically grouped into **process groups** and can be controlled by job control signals such as `SIGTERM` (terminate), `SIGHUP` (hang up), etc.
### 7. **Session Management in Virtualization/Containers**
- In environments like Docker or virtual machines, sessions refer to the time period when a user or process interacts with a virtual instance or container. Each container or VM operates within its own session and namespace, isolated from others.
### Commands to Manage Sessions:
- **`who`**: Shows users currently logged in.
- **`w`**: Displays active user sessions along with what they are doing.
- **`ps`**: Displays process information, including sessions and groups.
- **`loginctl`** (Linux): Manages and inspects user sessions.
- **`kill`**: Used to terminate a session by killing processes related to it.