


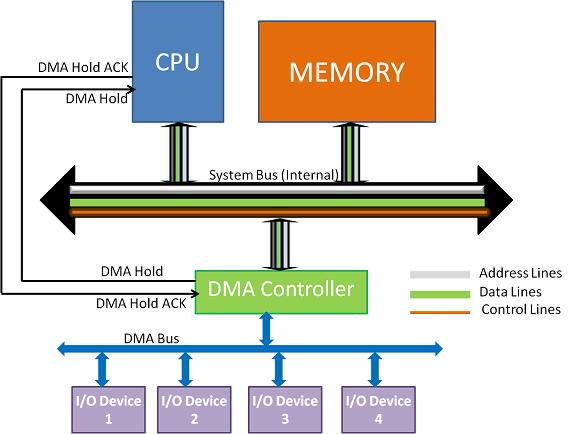
1.What is a DMA Controller?
=> Direct Memory Access uses hardware for accessing the memory, that hardware is called a DMA Controller. It has the work of transferring the data between Input Output devices and main memory with very less interaction with the processor. The direct Memory Access Controller is a control unit, which has the work of transferring data.
2.Types of Direct Memory Access (DMA).
=> There are four popular types of DMA.
Single-Ended DMA
Dual-Ended DMA
Arbitrated-Ended DMA
Interleaved DMA
•Single-Ended DMA: Single-Ended DMA Controllers operate by reading and writing from a single memory address. They are the simplest DMA.
•Dual-Ended DMA: Dual-Ended DMA controllers can read and write from two memory addresses. Dual-ended DMA is more advanced than single-ended DMA.
•Arbitrated-Ended DMA: Arbitrated-Ended DMA works by reading and writing to several memory addresses. It is more advanced than Dual-Ended DMA.
•Interleaved DMA: Interleaved DMA are those DMA that read from one memory address and write from another memory address.
3.Modes of Data Transfer in DMA.
=> There are 3 modes of data transfer in DMA that are described below.
••Burst Mode: In Burst Mode, buses are handed over to the CPU by the DMA if the whole data is completely transferred, not before that.
••Cycle Stealing Mode: In Cycle Stealing Mode, buses are handed over to the CPU by the DMA after the transfer of each byte. Continuous request for bus control is generated by this Data Transfer Mode. It works more easily for higher-priority tasks.
••Transparent Mode: Transparent Mode in DMA does not require any bus in the transfer of the data as it works when the CPU is executing the transaction.
4.Advantages and disadvantages of DMA Controller.
=>
a. Advantages of DMA Controller
i.Data Memory Access speeds up memory operations and data transfer.
ii. CPU is not involved while transferring data.
iii. DMA requires very few clock cycles while transferring data.
iv. DMA distributes workload very appropriately.
v. DMA helps the CPU in decreasing its load.
b. Disadvantages of DMA Controller
i.Direct Memory Access is a costly operation because of additional operations.
ii. DMA suffers from Cache-Coherence Problems.
iii. DMA Controller increases the overall cost of the system.
iv. DMA Controller increases the complexity of the software.