


In computer systems, efficient data transfer between the processor and peripherals is crucial. Among the various techniques for managing I/O operations, Direct Memory Access (DMA) stands out as the most efficient, particularly for handling large data volumes. Let’s explore how DMA works and why it surpasses methods like programmed I/O and interrupt-driven I/O.
Traditional I/O Methods:-
Programmed I/O involves the processor issuing a command to the I/O module and waiting for the operation to complete by continuously checking the module’s status. This method is inefficient because it ties up the processor, preventing it from performing other tasks.
Interrupt-driven I/O improves upon this by allowing the processor to issue an I/O command and continue with other work. The I/O module interrupts the processor when it’s ready to transfer data. Although more efficient than programmed I/O, it still requires the processor to manage data transfers, limiting the transfer rate and keeping the processor involved .
How DMA Works:-
DMA offers a more efficient approach by minimizing processor involvement. Here’s how it works:
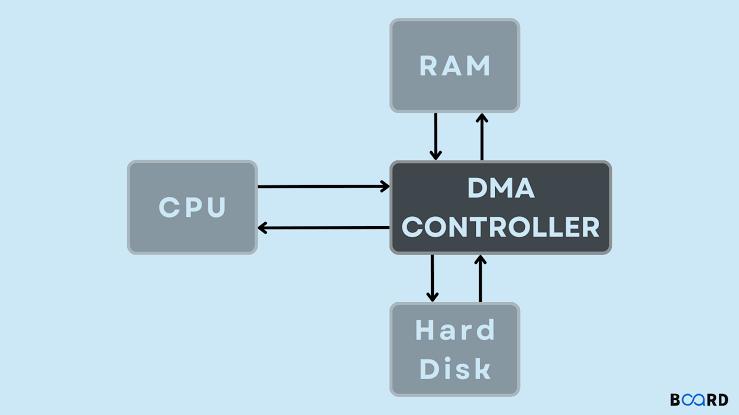
1. Command Issuance: The processor sends a command to the DMA module, specifying the operation type (read/write), the I/O device address, the starting memory location, and the number of words to transfer.
2. Independent Operation: The DMA module takes over, transferring data directly between memory and the I/O device without involving the processor. This direct transfer bypasses the processor, allowing it to focus on other tasks.
3. Completion Notification: Once the transfer is complete, the DMA module sends an interrupt signal to the processor, indicating the operation's end.
Advantages of DMA
DMA’s primary advantage is its efficiency. By offloading the data transfer task from the processor, DMA significantly boosts system performance, especially for large data volumes. Key benefits include:
- Reduced Processor Involvement: The processor only handles the initiation and completion of the transfer, freeing it for other tasks.
- Direct Transfers: Data moves directly between memory and the I/O device, bypassing the processor and speeding up the process.
In summary, DMA is the superior method for I/O operations, providing significant efficiency gains by reducing processor involvement and enabling direct data transfers.
Dhanish Soni