


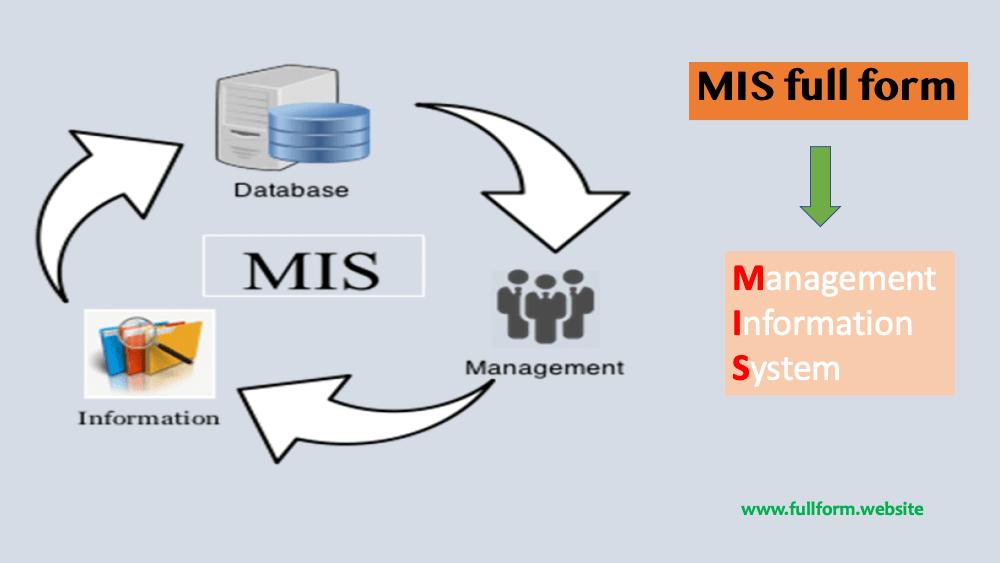
1) Management information systems (MIS) are used by tactical administration to supervise the association's present performance status. The information given by MIS can be used to construct small decisions
2) MIS takes data from transaction processing system and produces unchanging reports
3) For example, data about last month's deals facilitate to identify which the goods are selling in highest number and which goods not selling in highest number
4) This information can be used to optimise store and also build up method to enhance sales of goods which are not selling in highest number
5) Examples of MIS consists of human resources management system, sales management system, budgeting system etc.