


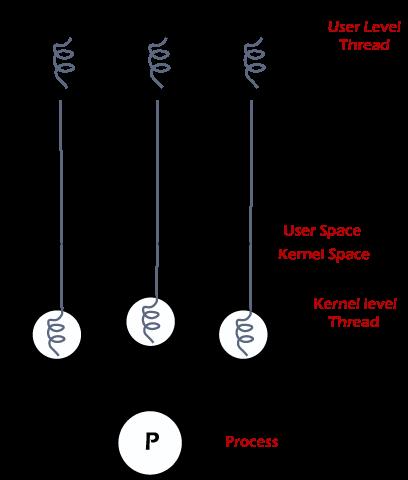
In operating systems, threads are the smallest unit of execution within a process. They can be categorized into several types based on different criteria:
User-Level Threads (ULTs):
Managed by user-level libraries or runtime systems.
The operating system kernel is unaware of these threads.
Switching between ULTs is fast since it doesn't involve the kernel, but these threads are not suitable for taking advantage of multiprocessor systems since the kernel cannot manage them.
Kernel-Level Threads (KLTs):
Managed directly by the operating system kernel.
The kernel is aware of and schedules these threads.
Provides better support for multiprocessor systems as the kernel can distribute threads across processors.
Switching between KLTs involves kernel intervention, which can be slower compared to ULTs.
Hybrid Threads:
Combine aspects of both user-level and kernel-level threading.
Often implemented using a model where user-level threads are mapped to kernel-level threads, allowing better flexibility and performance.
Lightweight Processes (LWPs):
A term used in some systems to refer to threads that are managed by the kernel and have their own scheduling and resource management.
LWPs provide a mechanism to efficiently utilize multi-core processors.
Real-Time Threads:
Designed to meet specific timing constraints and deadlines.
Used in real-time operating systems where timely execution is critical.
These thread types help in managing tasks efficiently, improving performance, and leveraging multi-core processors based on the system requirements.