


A deadlock occurs when every member of a set of processes is waiting for an event that can only be caused by a member of the set. Often the event waited for is the release of a resource. In the automotive world deadlocks are called gridlocks.
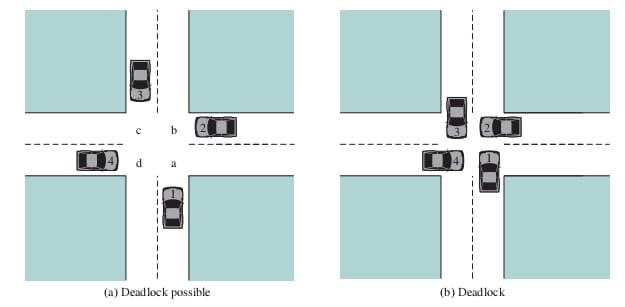
All deadlocks involve conflicting needs for resources by two or more processes. A common example is the traffic deadlock. The following figure shows a situation in which four cars have arrived at a four-way stop intersection at approximately the same time. The four quadrants of the intersection are the resources over which control is needed. In particular, if all four cars wish to go straight through the intersection, the resource requirements are as follows:
• Car 1, traveling north, needs quadrants a and b.
• Car 2 needs quadrants b and c.
• Car 3 needs quadrants c and d.
• Car 4 needs quadrants d and a
Following are the four strategies used for dealing with deadlocks:-
1. Ignore the problem.
2. Detect deadlocks and recover from them.
3. Avoid deadlocks by carefully deciding when to allocate resources.
4. Prevent deadlocks by violating one of the 4 necessary conditions.