


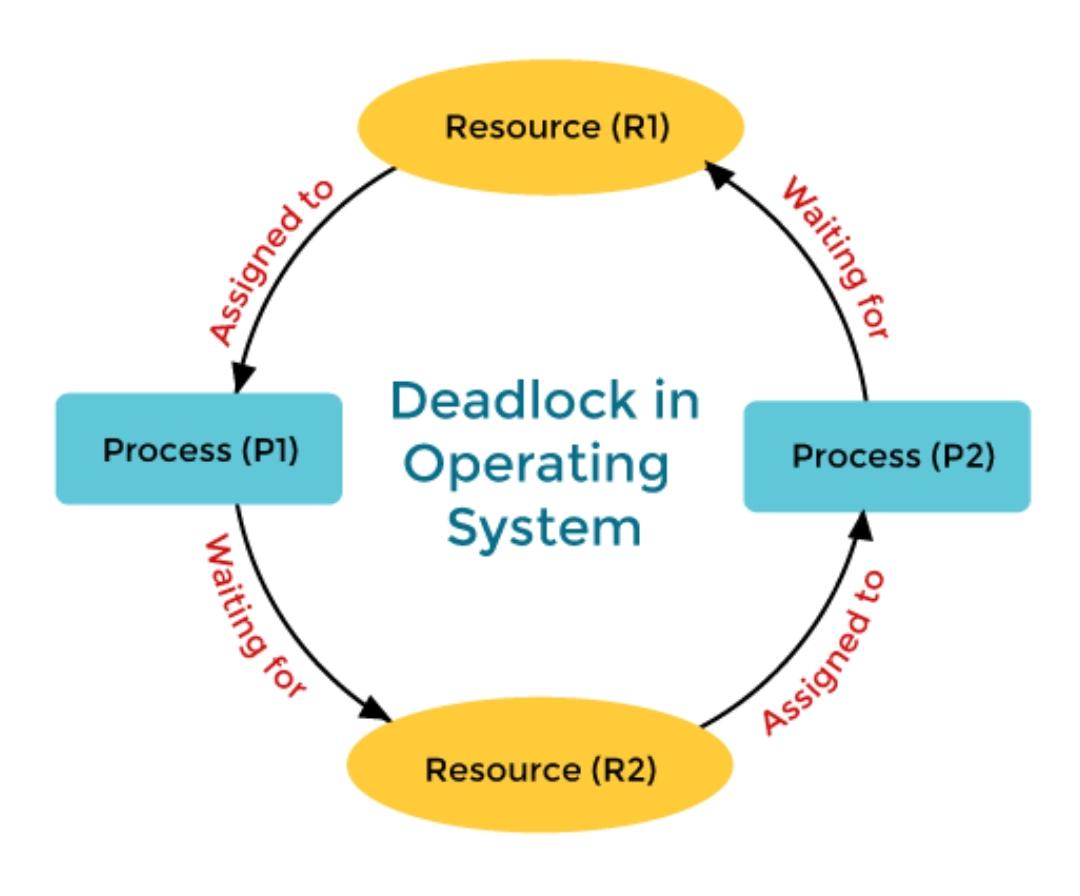
Deadlock is a situation in computing where two or more processes are unable to proceed because each is waiting for the other to release resources. Key concepts include mutual exclusion, resource holding, circular wait, and no preemption.
Consider an example when two trains are coming toward each other on the same track and there is only one track, none of the trains can move once they are in front of each other. This is a practical example of deadlock.
How Does Deadlock occur in the Operating System?
Before going into detail about how deadlock occurs in the Operating System, let’s first discuss how the Operating System uses the resources present. A process in an operating system uses resources in the following way.
Requests a resource
Use the resource
Releases the resource