


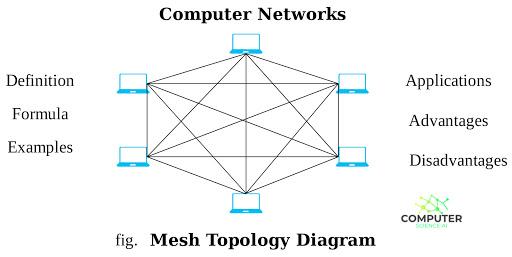
In this layout, every system is connected to every other system. The main advantage of this topology is high availability. The main disadvantage of this topology is cost, both administrative and physical. Because each system is connected to each other, the amount of cabling and maintenance necessary can be prohibitive, especially in larger networks.
This topology is mainly used in Wide Area Network environments or in environments where high availability outweighs the costs associated with this amount of interconnection.A wireless mesh network is made up of three or more wireless access points, working in harmony with each other while sharing each other routing protocols, in a collection of cross-connect links to create an interconnected electronic pathway for the transmission between two or more computers. When a wireless mesh is form it creates a single name identifier for access and the signals between wireless access points are used with each other to clearly distinguishable from another network. The organization of sharing access points working in harmony is known as the mesh topology. The defined mesh topology of a given area defined by the access points is known as mesh cloud. Access to this mesh cloud is dependent on the network created by the access points.