


A computer system threat is anything that leads to loss or corruption of data or physical damage to the hardware of infrastructure. It is the first step to know how to identify security threats to protect the computer system.
Types of threats
security threats
physical threats
Non physical threats.
1) Security threats:- Security threat is defined as a risk that which can potentially harm computer system. The cause could be physical such as someone stealing a computer that contains vital data. The cause could also be non-physical such as virus attack.
2) Physical Threats:- A physical threat is a potential cause of an incident that may result in loss or physical damage to the computer system.
There are 3 main categories that classifies the physical threats.
Internal:- These Threats include fire, unstable power supply, humidity in the rooms housing the hardware etc.
External:- These threats include lightning, floods, earthquake etc.
Human:- These threats include theft, vandalism of the infrastructure or hardware, disruption accidental or Intentional errors.
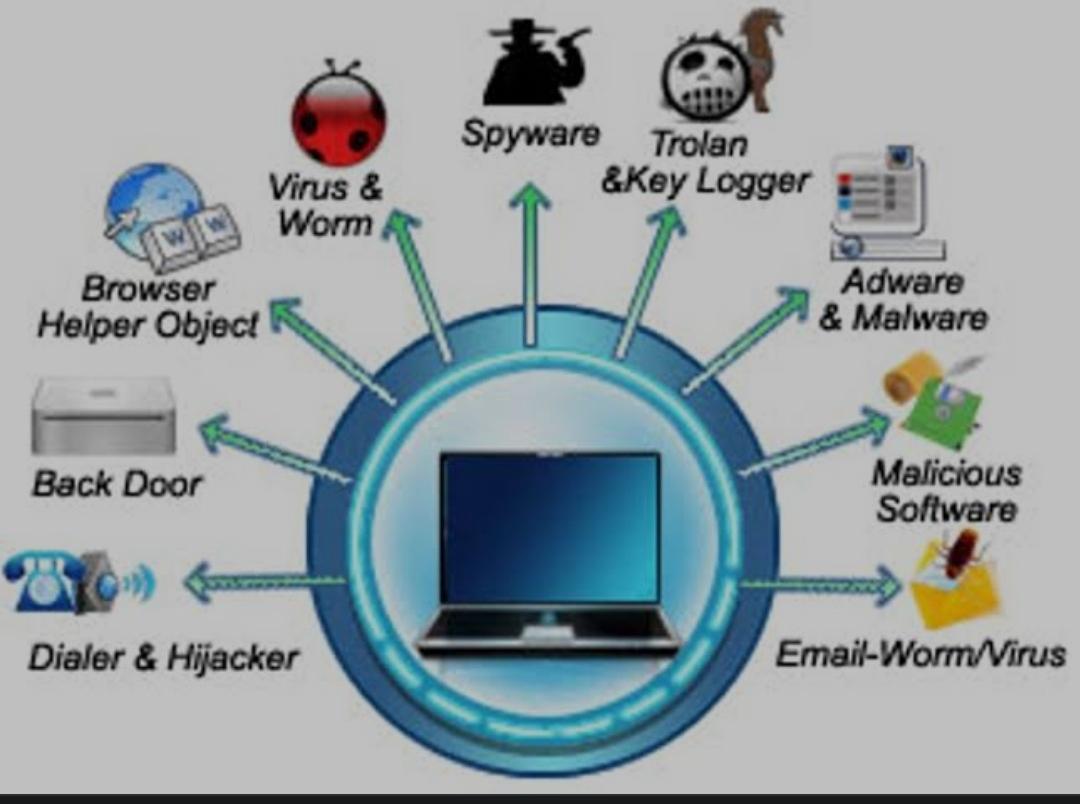
3) Non-physical Threats:- A non-physical threat is a potential cause of an incident that may result in.
loss or corruption of system data
loss of sensitive information
cyber security branches
others.
The non-physical threats are also known as logical Threats.
The following list is the common types of non-physical threats.
virus
key loggers
spyware
adware
phishing
worms
other computer security risks.