


operating system
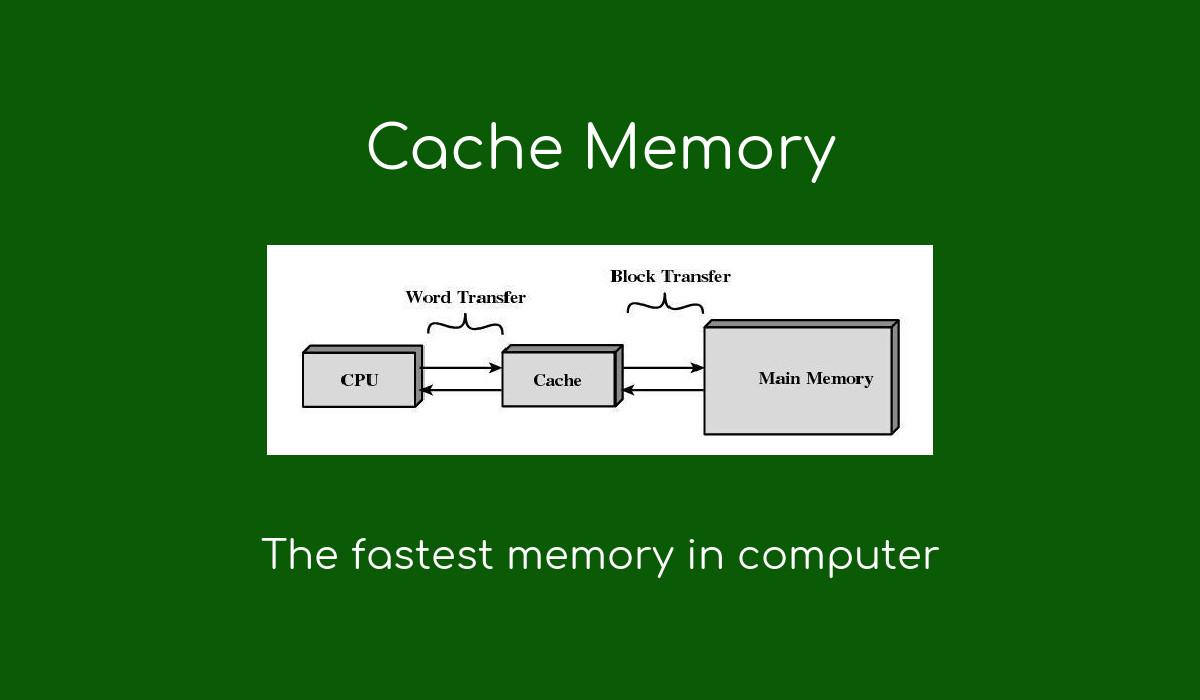
Operating system cache memory works like a superfast ephemeral storage which get between CPU (the brane of your computer) and main memory (RAM). Part is to do increase computer performance by saving frequently-used instructions and data as near to the CPU as possible for fast retrieval. Think about being in the middle of a project that you often work on using certain tools and resources. Rather than walking to and fro so as to fetch these from a far storage room get in on time